Cyber Resiliency Videos
Stay a Step Ahead of Cyberthreats
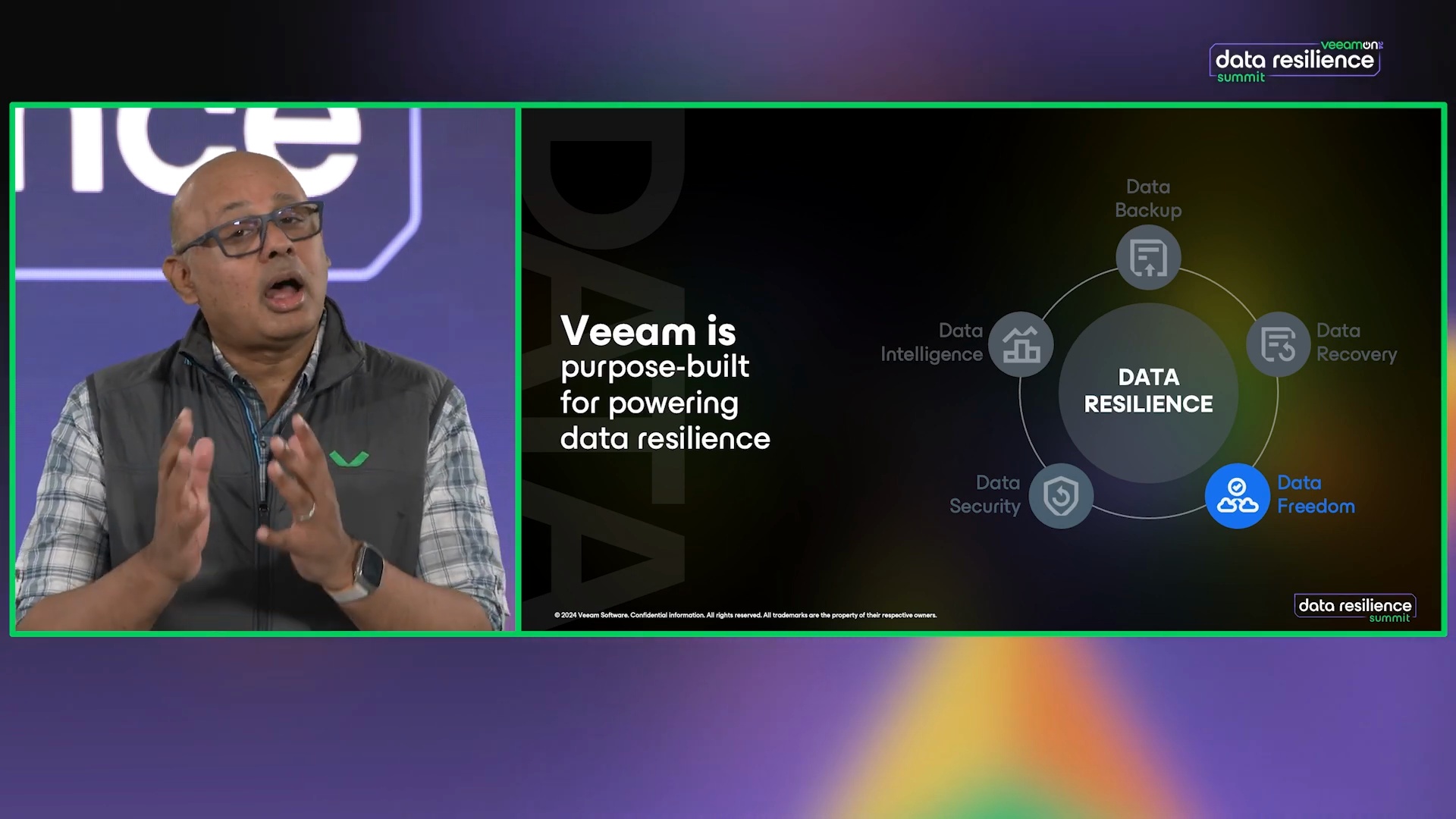
What is Data Resilience?
Anand Eswaran explores our approach to data resilience: Backup, Recovery, Portability, Security, and Intelligence.
Partnerships in Cybersecurity
Learn how collaboration between government and private sector enhances data resilience against evolving threats.
Local Governments Choose Veeam
Don't just take our word for it. Hear why agencies choose Veeam, time after time.
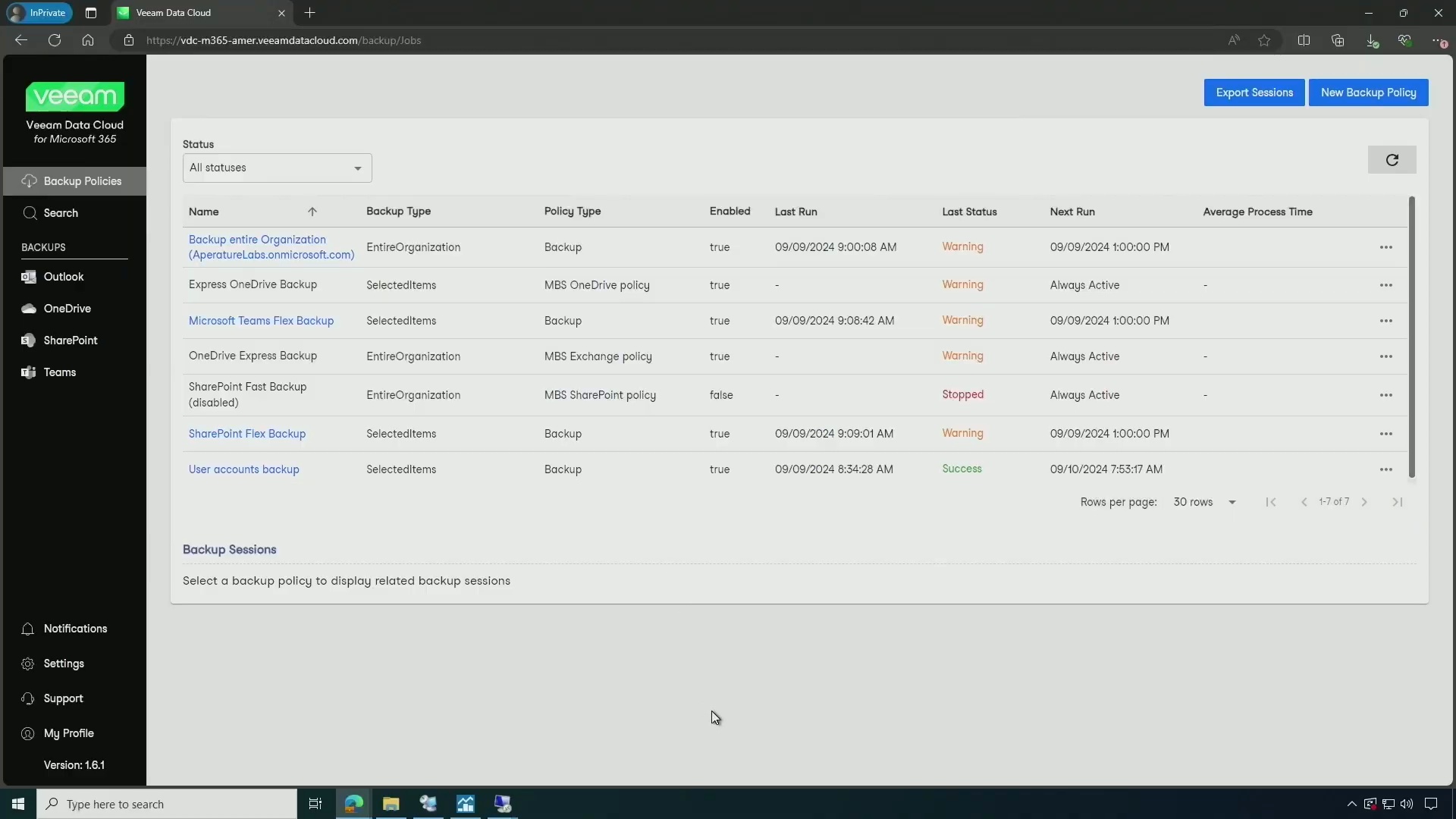
Veeam Data Cloud
Learn how seamless backup policies, performant storage options, and immutable repositories ensure security for your organization.
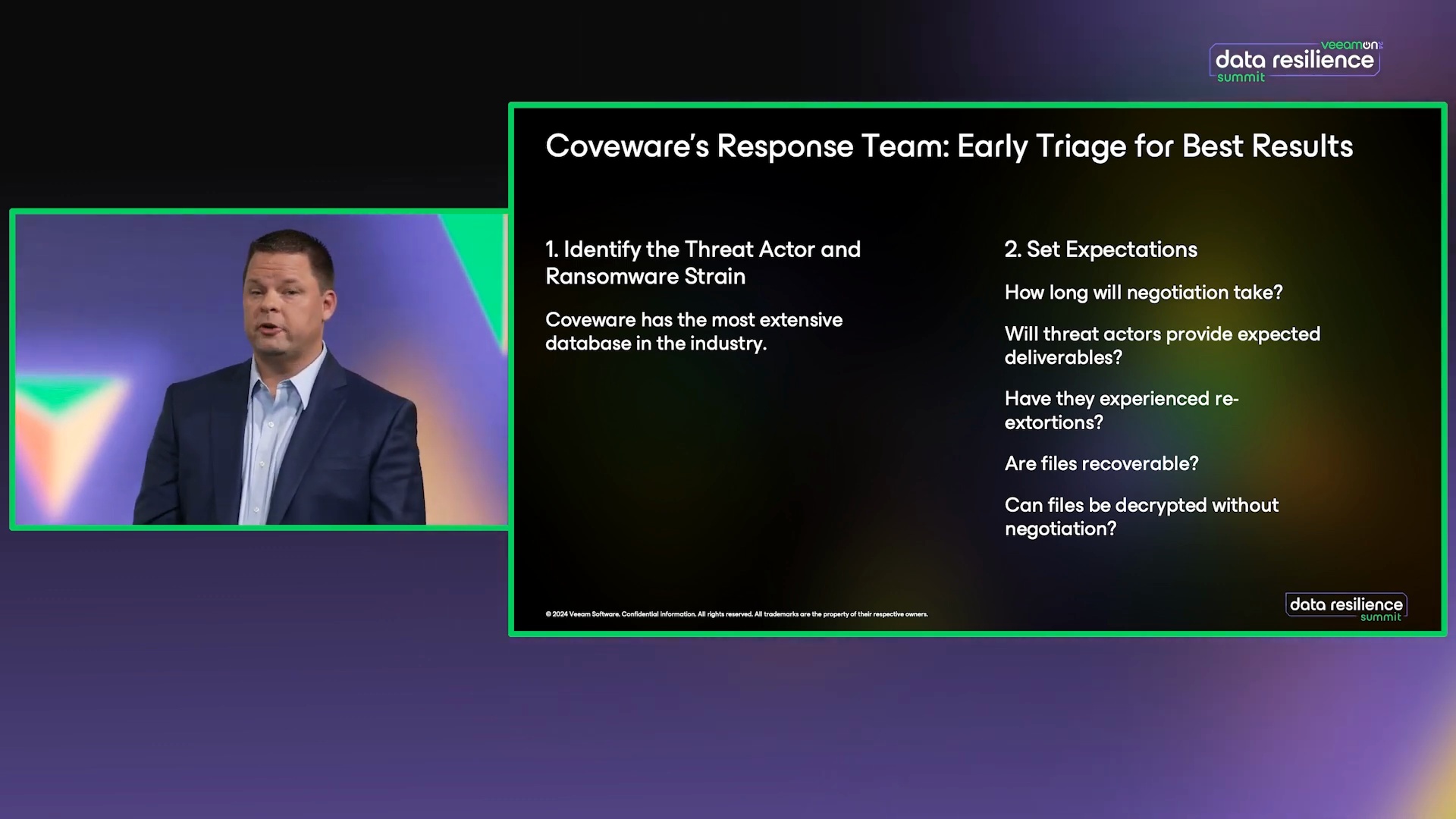
Veeam Cyber Secure & Coveware
Learn how Coveware by Veeam aids organizations during ransomware attacks, from proactive threat assessment to managing negotiations.
Recon Scanner: Ransomware Detection
Powered by Coveware, Recon Scanner is a proactive tool that detects ransomware before it activates, enhancing data security at no additional cost.
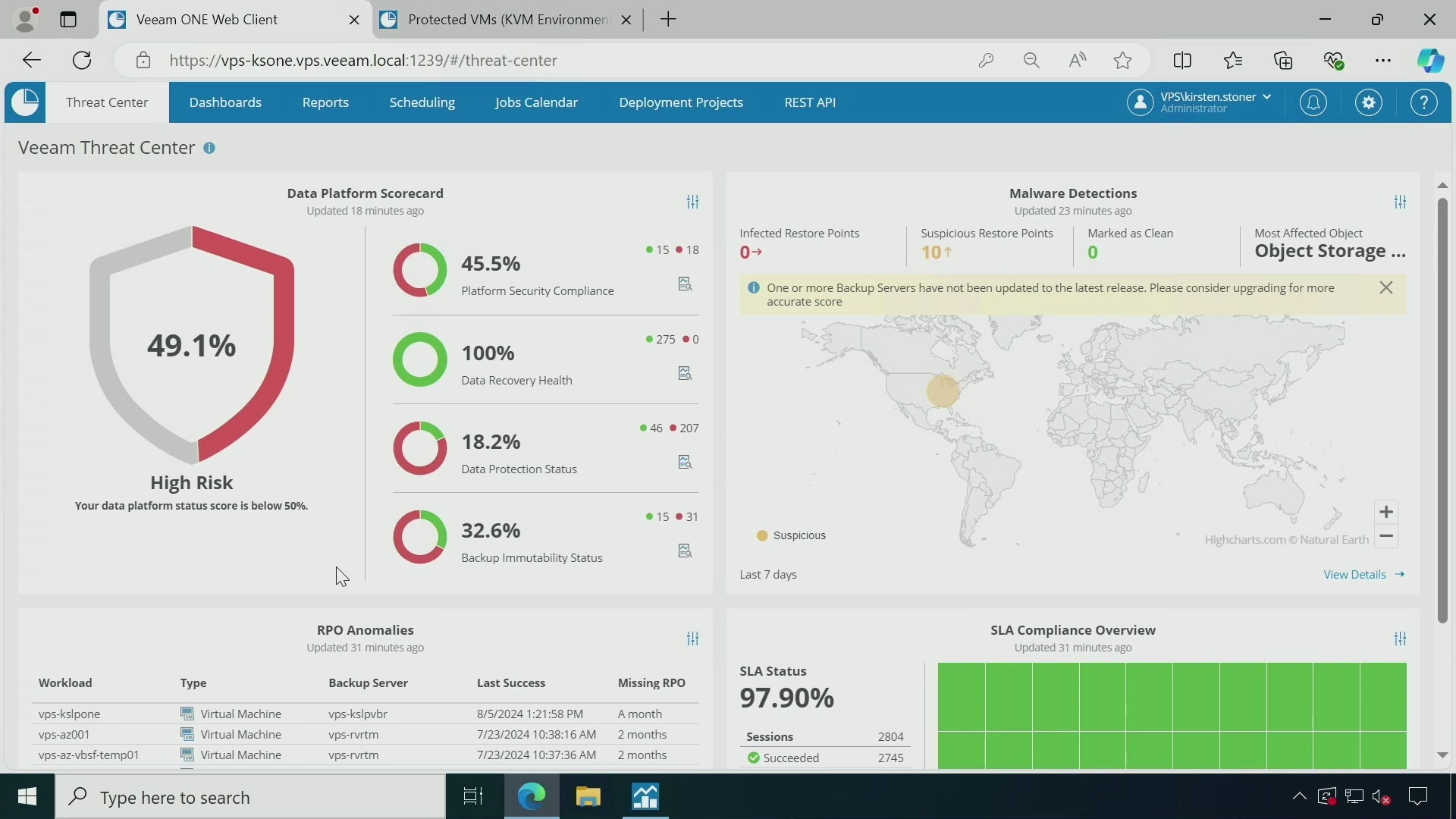
Simplified Workload Mobility & Monitoring
Veeam’s Data Portability features Proxmox support, enhanced monitoring through Veeam ONE, and Veeam Recovery Orchestrator.
Strengthening Cybersecurity Integration With Palo Alto
Learn about the partnership between Palo Alto Networks and Veeam, integrating Veeam to enhance and automate threat response.
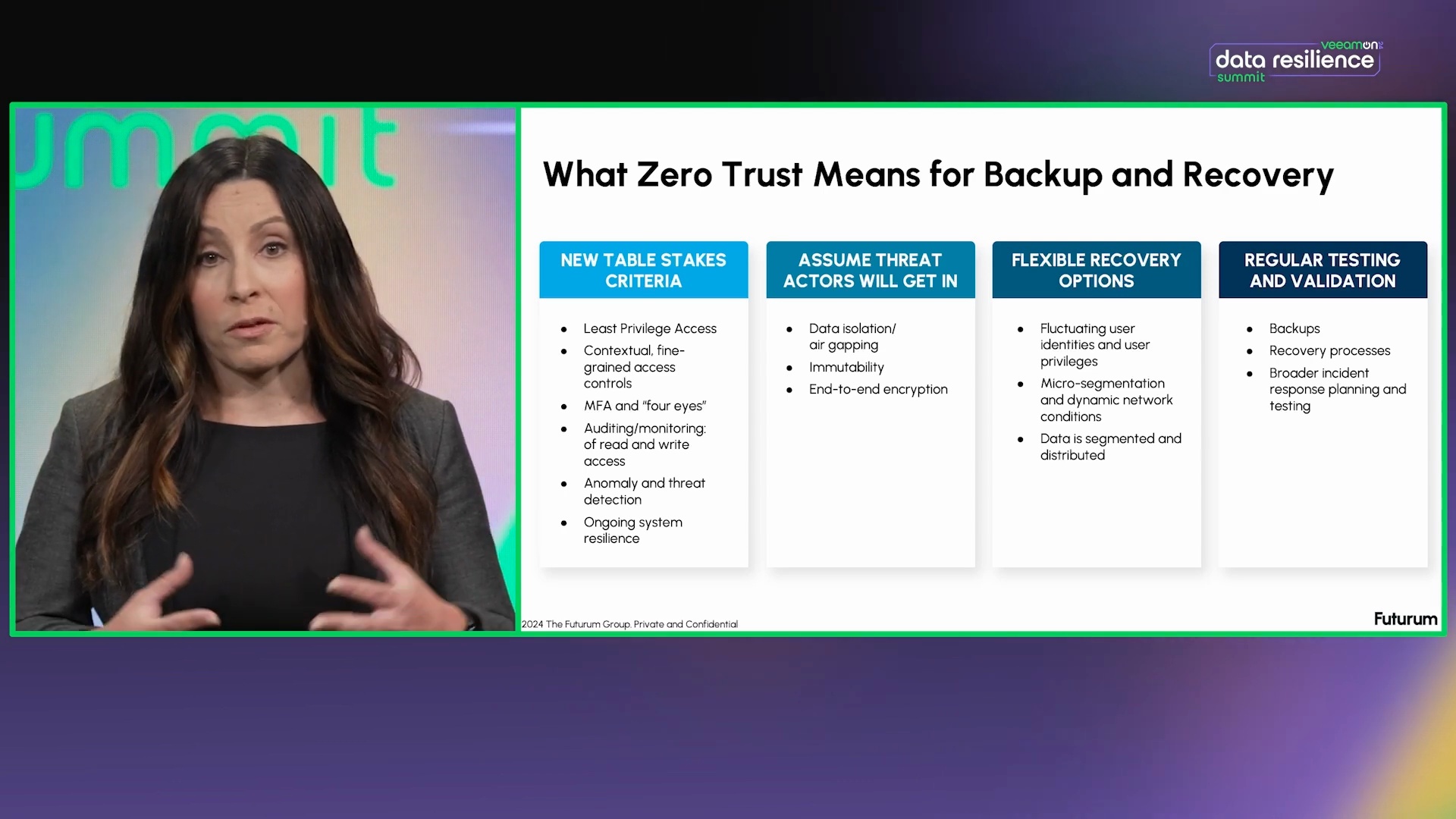
Zero Trust Data Resilience
Explained
Learn how Zero Trust principles reduce risks and enhance incident response.
Data Resilience Keeps Every Business Running
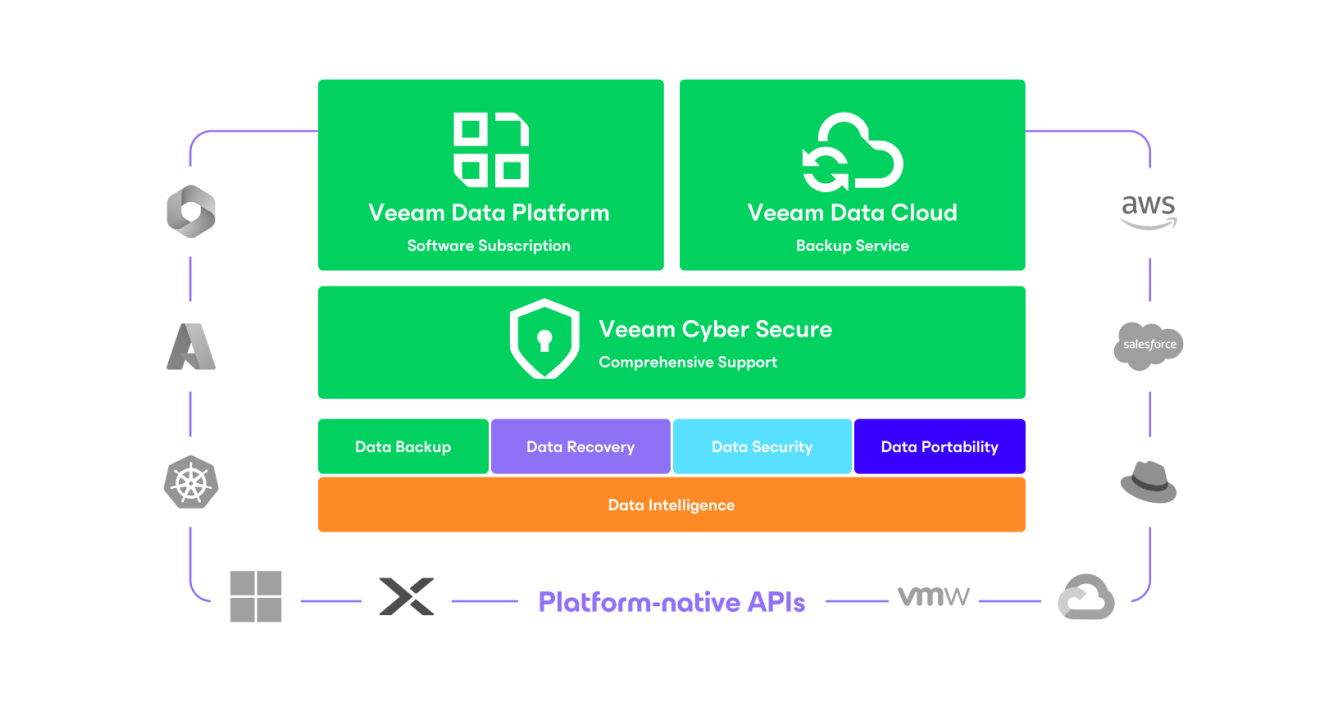
Veeam Data Platform
Powerful data resilience
- Integrity for your identity
- Resilience for your critical assets
- Evolution for your enterprise
Stay Up to Date on the Latest Data Security Trends

2024 Global Report: Ransomware Trends
Lessons learned from 1,200 victims and 2,500 cyberattacks, spotlighting actions taken to recover from the impact of cyber attacks.
2024 Ransomware Trends Report
Lessons learned from 1,200 victims and nearly 2,500 cyberattacks.
Elevating Data Security
Veeam’s commitment reinforcing data security and ensuring the confidentiality, integrity, and availability of sensitive information
Best Practices for Secure Hybrid and Multi-Cloud Backup
Protect and secure your data as a part of your cyber resiliency plan
7 Best Practices for Ransomware Recovery
Ready to make recovery your top priority? Get the leading edge on early threat detection and ensure fast recovery with orchestration.
Radical Resilience is Our Difference
hybrid cloud and the confidence you need for long-term success.
Learn the Latest Trends in Data Protection
Our 5th annual report summarizing data protection strategies