#1 Kubernetes Data Protection & Mobility
Veeam Kasten Free
Veeam Kasten for Kubernetes
#1 Kubernetes Data Protection & Mobility
- Recover entire applications
- Ensure security and resilience
- Application mobility across platforms
Trusted Kubernetes Data Protection
Recover Entire Applications
Rapidly recover entire applications – including underlying data and configuration – with confidence and ease.
Ensure Security and Resilience
Securely operate with built-in protection against cyberthreats with immutable, encrypted backups and self-service restores.
Application Mobility Across Platforms
Easily enable hybrid and multi-cloud operations with seamless application mobility across different infrastructure and distributions.
Explore Veeam Kasten for Kubernetes
Policy Automation
Efficiently manage entire application protection – including data inside and outside the cluster – at enterprise scale.
Granular Restore
Maintain total control over what artifacts and data to restore, including data-only restore for running applications.
Automated DR
Recreate entire application stacks into the same namespace, or a new one automatically.
Immutable & Encrypted
Safeguard data against ransomware and other threats by placing backups in an encrypted and WORM state.
Least Privilege Access
Granularly assign permissions to data protection operations and resources on a per-application level.
SIEM Integrations
Ingest and aggregate SIEM data for governance and real-time threat detection, investigation, and analysis.
Cross-Cloud Portability
Mobilize applications across namespaces, clusters, and clouds for DR, test/dev, and performance testing.
Transform Across Distributions
Easily modify the specific contents of K8s resources when restoring or migrating across environments.
VMs on Kubernetes
Migrate, modernize, and manage VMs on Kubernetes without refactoring the entire application.
Stay Updated With the Latest Kubernetes Insights and Trends
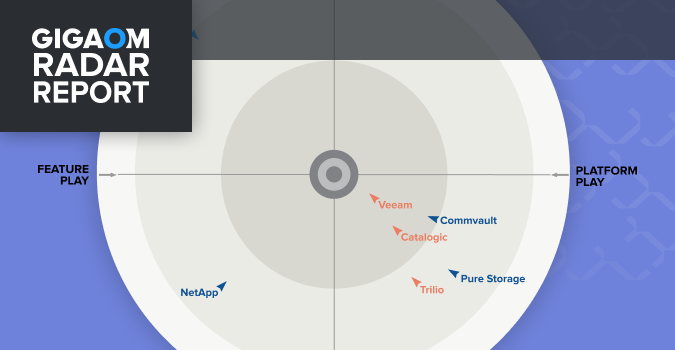
Veeam is a Four-Time Leader and Outperformer
Kubernetes applications require a Kubernetes-native approach, and Veeam’s solution outranks competitors.
Open Source vs. Enterprise Data Protection
Explore the difference in features, capabilities, and functionality between the two industry-leading Kubernetes data protection tools.
5 Kubernetes Backup Best Practices
Kubernetes has emerged as the de-facto container orchestration platform. Learn how to address its unique data management needs.
Kubernetes Backup and Recovery For Dummies
Backup in Kubernetes is different. This book is packed with actionable steps you can take to protect your data.
Documentation
Additional Resources
Veeam Kasten for Kubernetes v7.5
- Enterprise-scale resilience
- Expanded security and compliance
- Modern virtualization
FAQs
What is Veeam Kasten for Kubernetes?
What free Veeam Kasten versions are available?
Can the Veeam Kasten free version be converted to a true enterprise license?
Radical Resilience is Our Difference
hybrid cloud and the confidence you need for long-term success.