How to Exclude Applications from Dashboard & Compliance Reporting
Purpose
Solution
Explanation
Veeam Kasten for Kubernetes automatically discovers all application namespaces of the cluster on which it is deployed. Each of these discovered applications is listed on the Applications page within the Dashboard, along with its current Compliance status. Compliance metrics are also made available through built-in Veeam Kasten for Kubernetes Reports and Prometheus/Grafana.
Specific namespaces can be hidden both from the UI and compliance reporting. For instance, cluster infrastructure-related namespaces are typically not protected by Veeam Kasten for Kubernetes and are instead restored via Infrastructure as Code tools or scripts (e.g., operators). Doing so may provide more meaningful compliance reporting, whereas Unmanaged namespaces could lead to additional investigation to ensure applications are adequately protected.
NOTE: An Unmanaged status indicates that an application is not protected by any Veeam Kasten for Kubernetes policy. A Compliant status indicates that one or more policies protect an application and that the available RestorePoints meet the specified frequency and retention. A Non-Compliant status would indicate an issue, such as policy runs failing due to an infrastructure problem.
Helm-based Installation of Veeam Kasten for Kubernetes
For a Helm installation of K10 (assumes default k10 release name and kasten-io namespace):
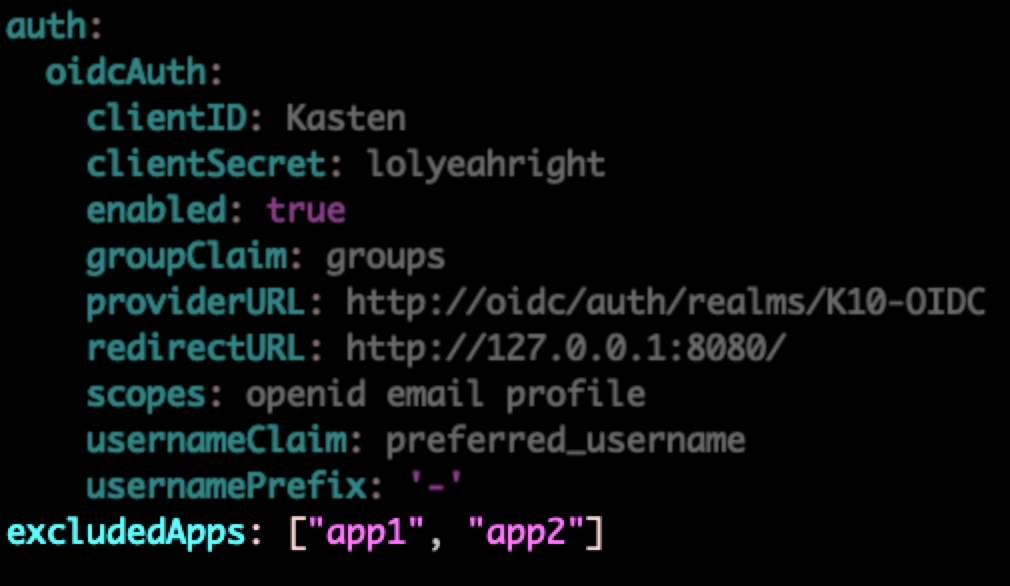
Predefined App Exclusion Examples
Certain distributions, such as Red Hat OpenShift and vSphere Tanzu produce many “system” namespaces which can be excluded if needed.
The following commands can be used to quickly populate a list and append to the k10_val.yaml file:
- Kubernetes
- Openshift
- Tanzu
Operator-based Installation of Veeam Kasten for Kubernetes
In the OpenShift console, under Installed Operators, select the YAML tab of the K10 instance.
Search for excludedApps: and specify the list of namespaces as an inline or multi-line YAML array:
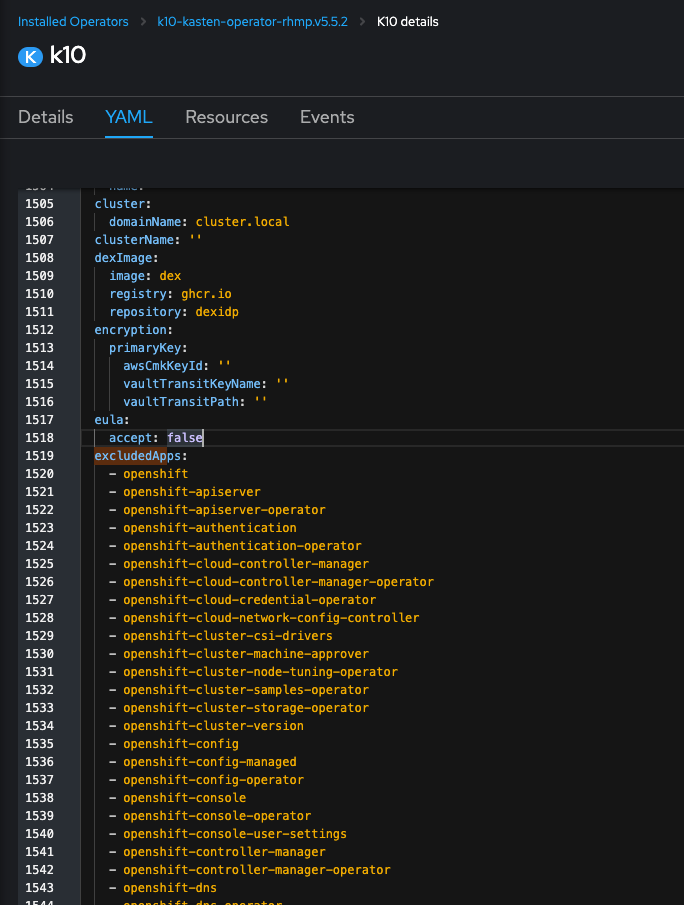
Click Save to apply.
The following command can be used to quickly populate a list properly formatted to copy/paste into the YAML form in the OpenShift console:
To report a typo on this page, highlight the typo with your mouse and press CTRL + Enter.
Spelling error in text
KB Feedback/Suggestion
This form is only for KB Feedback/Suggestions, if you need help with the software open a support case