WDAC Supplemental Policy for Veeam Backup & Replication Components on Azure Stack HCI
Challenge
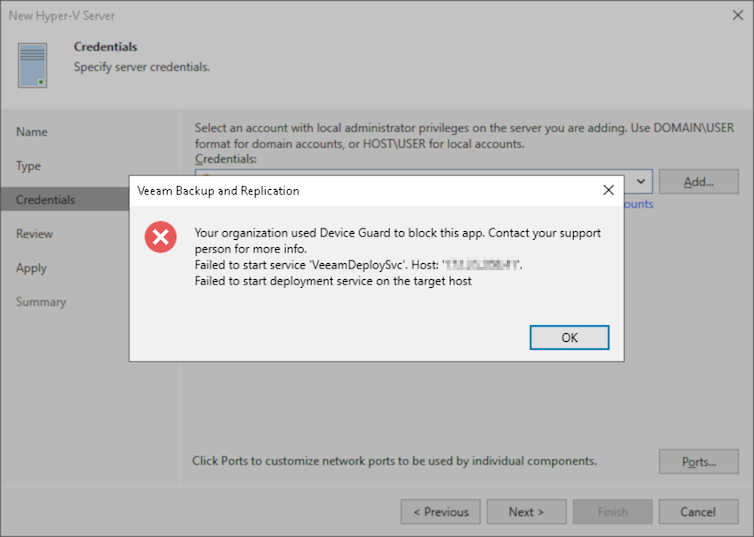
When attempting to add an Azure Stack HCI OS cluster or node to Veeam Backup & Replication, the following error occurs:
Your organization used Device Guard to block this app. Contact your support person for more info. Failed to start service 'VeeamDeploySvc'. Host: 'x.x.x.x'. Failed to start deployment service on the target host
Cause
By default, Azure Stack HCI OS 23H2 and newer has Windows Defender Application Control (WDAC) enabled and running in the enforcement mode. WDAC is a software-based security layer that reduces the attack surface by enforcing an explicit list of software that is allowed to run. WDAC limits the applications and the code that can run on the core platform.
To allow third-party non-Microsoft signed software to run on Azure Stack HCI nodes, a WDAC supplemental policy provided by the third-party software vendor must be installed.
Solution
Veeam Backup & Replication WDAC Supplemental Policy Deployment
- Download the Policy XML Package from the Download Information section below.
- Copy the policy XML file to a location on the CSV (Cluster Shared Volume) shared by the nodes.
- Deploy the policy using Add-ASWDACSupplementalPolicy cmdlet.
This can also be done using the latest version of Windows Admin Center.
Example command output:
VERBOSE: Fetching Supplemental Policy from C:\ClusterStorage\Infrastructure_1\wdac\KB4456\VBR-AZHCI-supplemental-policy-1.0.0.2.xml.
VERBOSE: Checking the XML file C:\ClusterStorage\Infrastructure_1\wdac\KB4456\VBR-AZHCI-supplemental-policy-1.0.0.4.xml
VERBOSE: Staging the Supplemental Policy VBR-AZHCI-supplemental-policy-1.0.0.4.xml.
VERBOSE: Convert VBR-AZHCI-supplemental-policy-1.0.0.4.xml to {48D8AD47-2B5F-4134-8C68-C320DC2D116A}.cip.
VERBOSE: Handling the supplemental policy {48D8AD47-2B5F-4134-8C68-C320DC2D116A}.cip on HOST1.
VERBOSE: Refresh WDAC Policy on HOST1.
VERBOSE: WDAC Policy Refreshing Succeeded!
VERBOSE: Fetching results from the events.
VERBOSE: Refreshed and activated Code Integrity policy {48d8ad47-2b5f-4134-8c68-c320dc2d116a} VBR_Supplemental_Policy. id VBR_Supplemental_Policy_1.0.0.4. Status 0x0
VERBOSE: No change in active Code Integrity policy {7c901c27-99d2-4add-9494-5e79f16c345e} AzCli_Supplemental_Policy after refresh. id AzCli_Supplemental_Policy_20231006. Status 0x0
VERBOSE: No change in active Code Integrity policy {a6368f66-e2c9-4aa2-ab79-8743f6597683} AS_Base_Policy after refresh. id AS_Base_Policy_1.2.5.0. Status 0x0
VERBOSE: Handling the supplemental policy {48D8AD47-2B5F-4134-8C68-C320DC2D116A}.cip on HOST2.
VERBOSE: Refresh WDAC Policy on HOST2.
VERBOSE: WDAC Policy Refreshing Succeeded!
VERBOSE: Fetching results from the events.
VERBOSE: Refreshed and activated Code Integrity policy {48d8ad47-2b5f-4134-8c68-c320dc2d116a} VBR_Supplemental_Policy. id VBR_Supplemental_Policy_1.0.0.4. Status 0x0
VERBOSE: No change in active Code Integrity policy {7c901c27-99d2-4add-9494-5e79f16c345e} AzCli_Supplemental_Policy after refresh. id AzCli_Supplemental_Policy_20231006. Status 0x0
VERBOSE: No change in active Code Integrity policy {a6368f66-e2c9-4aa2-ab79-8743f6597683} AS_Base_Policy after refresh. id AS_Base_Policy_1.2.5.0. Status 0x0
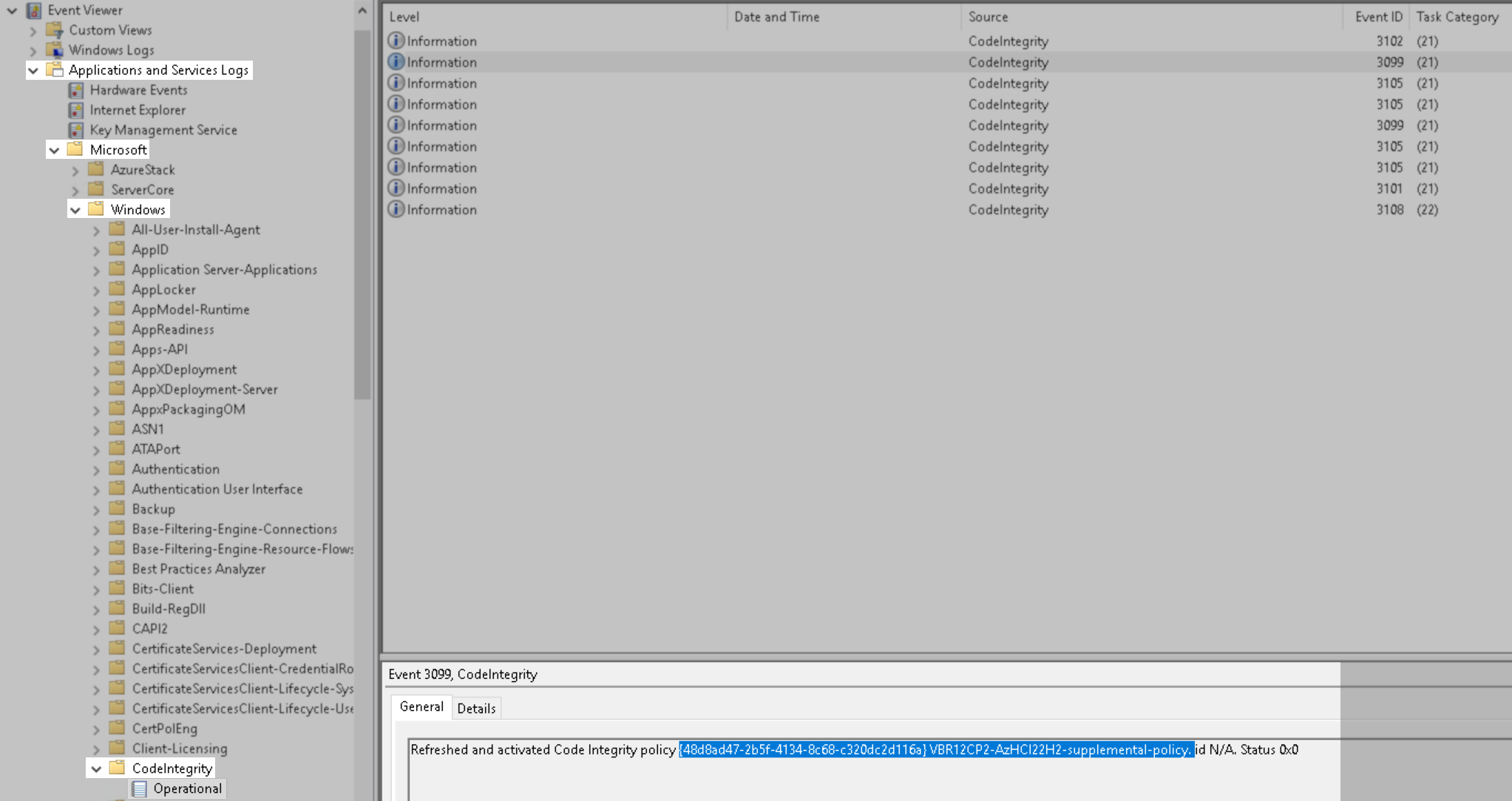
- Check Windows event logs to determine if the policy has been activated. Either:
- From a node using PowerShell:
- Open Event Viewer on a remote server and connect to a node, then check under:
Application and Services Logs > Microsoft > Windows > CodeIntegrity > Operational
Download Information
To report a typo on this page, highlight the typo with your mouse and press CTRL + Enter.
Spelling error in text
KB Feedback/Suggestion
This form is only for KB Feedback/Suggestions, if you need help with the software open a support case