Access to Hyper-V or Veeam B&R Components Fails After DCOM Hardening is Enabled
| KB ID: | 4376 |
| Product: |
Veeam Backup & Replication Veeam ONE Veeam Agent for Microsoft Windows Veeam Management Pack for Microsoft System Center Veeam Recovery Orchestrator |
| Published: | 2022-11-04 |
| Last Modified: | 2025-01-24 |
| Languages: | JP |
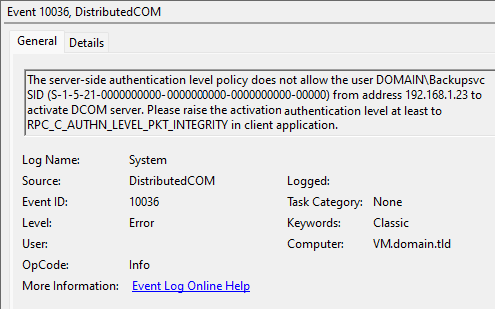
The issue discussed in this article is not identified solely based on the Veeam errors but rather by their correlation with Windows Event ID# 10036, which states:
The server-side authentication level policy does not allow the user from address <IP> to activate DCOM server.
Please raise the activation authentication level at least to RPC_AUTHN_LEVEL_PKT_INTEGRITY in client application.
The Veeam-level errors mentioned in this article may occur for other reasons. However, if they occur alongside Windows Event ID# 10036, then the underlying cause is DCOM hardening related.
Challenge
After June 14, 2022, DCOM connections to Hyper-V, Veeam Backup & Replication, and other Windows-based servers may be impacted by the DCOM hardening policy activated after the deployment of the Microsoft CVE-2021-26414 security update.
Below are examples of errors that may be shown by Veeam products affected by this:
This list of examples errors is not exhaustive, others may exist. It is critical to focus on checking for Windows Event ID 10036.
- Veeam Backup & Replication — operations involving Hyper-V infrastructure may fail with the error:
Failed to call RPC function 'HviCreateVmRecoverySnapshot'
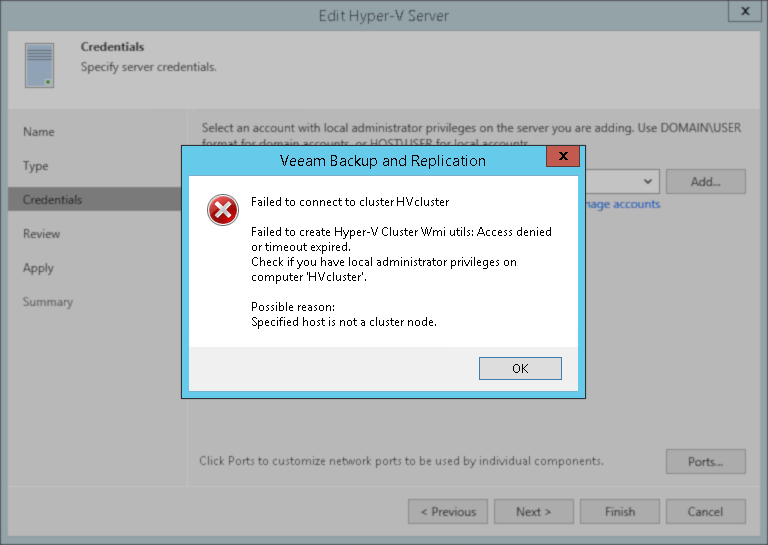
Failed to connect to cluster <clustername> Failed to create Hyper-V Cluster Wmi utils: Access denied or timeout expired. Check if you have local administrator privileges on computer '<clustername>'. Possible reason: Specified host is not a cluster node.
Failed to connect to host vmhost2 Access denied or timeout expired. Check if you have local administrator privileges on computer '<hostname>'. Possible reasons: 1. Invalid credentials. 2. Specified host is not a Hyper-V server.
- Veeam Agent for Microsoft Windows — connection to Hyper-V infrastructure fails with error:
Failed to connect to cluster 'CLUSTERNAME.contoso.com'.
- Veeam ONE — connection to Hyper-V and Veeam Backup & Replication infrastructures fails with the error:
System.UnauthorizedAccessException:'Access denied. (Exception from HRESULT : 0x80070005 (E_ACCESSDENIED))'
- Veeam Recovery Orchestrator — connection to Veeam Backup & Replication fails with the error:
Failed to connect to the server. Specified user is invalid or does not have enough permissions on the server.
Cause
| Update Release | Behavioral Change |
| June 8, 2021 | Hardening changes are disabled by default but with the ability to enable them using a registry key. |
| June 14, 2022 | Hardening changes are enabled by default but with the ability to disable them using a registry key. |
| March 14, 2023 | Hardening changes are enabled with no ability to disable them. By this point, you must resolve any compatibility issues with the hardening changes and applications in your environment. |
All Veeam products are prepared for this change and utilize Packet Integrity DCOM authentication level.
However, if the underlying Windows operating systems do not have the necessary security updates, this can lead to different authentication levels being used for DCOM connections, resulting in authentication failures. For instance, one Windows machine may have the hardening changes disabled due to the absence of the installed update, while another Windows machine may have the DCOM hardening enabled because the update is installed. When these DCOM authentication failures occur, Event #10036 will appear, displaying the following message:
Please raise the activation authentication level at least to RPC_C_AUTHN_LEVEL_PKT_INTEGRITY in client application
Solution
All Veeam products are ready for this DCOM change and use Packet Integrity DCOM authentication; the underlying Windows OS must be updated to support this change.
To resolve these issues, ensure all Windows-based servers have installed the DCOM Hardening update. See the list at the bottom of this article: KB5004442—Manage changes for Windows DCOM Server Security Feature Bypass (CVE-2021-26414).
The updates listed on that page may have been rolled in to future updates, check Windows DCOM Server Security Feature Bypass CVE-2021-26414 for more information.
Notes:
- These updates may be listed as optional and may have been ignored by Windows or WSUS systems. In such a situation, the update must be deployed manually.
- This issue may affect older Windows operating system, but the update to resolve the issue may not be available without ESU.
- For environments where Veeam Backup & Replication was deployed on an older operating system no longer supported by the latest version of Veeam Backup & Replication (e.g., Server 2008 R2), please review: KB1803: How to Upgrade Legacy Veeam Backup Server
To report a typo on this page, highlight the typo with your mouse and press CTRL + Enter.
Spelling error in text
KB Feedback/Suggestion
This form is only for KB Feedback/Suggestions, if you need help with the software open a support case