- Veeam Support Knowledge Base
- Veeam Backup for Office 365 Complete Permissions
Veeam Backup for Microsoft 365 Complete Permissions
Cheers for trusting us with the spot in your mailbox!
Now you’re less likely to miss what’s been brewing in our knowledge base with this weekly digest
Oops! Something went wrong.
Please, try again later.
The content of this article is being transitioned to the Veeam Backup for Microsoft 365 User Guide.
An up-to-date list of Required Permission is available in the Veeam Backup for Microsoft 365 User Guide.
Authentication Modes Summary
Depending on the Microsoft 365 account configuration and the restrictions on using legacy authentication protocols, one of the following authentication methods may be used:
- Modern app-only authentication
When you use this method, Veeam Backup for Microsoft 365 uses only the Azure AD application to authenticate to your Microsoft 365 organizations with enabled security defaults. You cannot use the Veeam Backup account with the modern app-only authentication method.
When protecting Microsoft 365 organizations using Modern App-Only Authentication mode, consider the limitations in backup and restore functionality listed in KB3146 - Modern authentication with legacy protocols allowed
When you use this method, you can use both the Veeam Backup account and Azure AD application to authenticate to your Microsoft 365 organizations with disabled security defaults. You use MFA-enabled Microsoft 365 user account as the Veeam Backup account. - Basic authentication
When you use this method, you are required to provide a user account as the Veeam Backup account to authenticate to your Microsoft 365 organization.
Microsoft is planning to deprecate Basic Authentication soon:
Authentication Mode Permissions
Modern App-Only Authentication
When you add Microsoft 365 organization using the modern app-only authentication method, you use only Azure AD application to establish and maintain connection between Veeam Backup for Microsoft 365 and Microsoft 365 organizations and perform a backup and restore from/to such organizations.
Azure AD Application Permissions
When adding a Microsoft 365 Organization using Modern app-only authentication you can create a new application in Azure Active Directory or select an existing one:
- Have Veeam Backup for Office 365 automatically create the Azure AD application and all the required application permissions will be granted automatically.
or - You can create an Azure AD application manually, then configure the permissions in accordance with "Requirements for Modern App-Only Authentication" section of the User Guide.
For more information about permission types please visit:
https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-permissions-and-consent
Modern Authentication with Legacy Protocols Allowed
When you add an organization using the modern authentication method with legacy protocols allowed, you use both Veeam Backup account and Azure AD application for authentication. Veeam Backup for Microsoft 365 uses Veeam Backup account and an application to establish a connection to your Microsoft 365 organizations with disabled security defaults and maintain data transfer during backup and restore sessions.
Before configuring permissions, please check the following things:
- Security Defaults are disabled in your Office 365 tenant.
- Conditional Access policies are not blocking legacy authentication protocols for the Veeam service account.
Section Table of Contents
- Configure Veeam service account permissions
- Configure the App password
- Configure Azure AD Application permissions
1. Veeam service account permissions
1.a. Exchange Role
Configuring permissions for Exchange Online.
- Create a role group in the Exchange Admin Center as explained here.
- Add Roles specified in the User Guide.
- Add the Veeam Service account to role group members and save the role group.
- Connect to the Exchange Online PowerShell module and run the "Get-AuthenticationPolicy" command.
- If there is a blank return, there is no policy, and you need to configure one.
- If the current policy does not list a value of "true" for AllowBasicAuthPowershell and AllowBasicAuthWebService, contact the Domain admins to update the policy with this Microsoft document.
Below is an example of PowerShell cmdlets that could be used to configure a new authentication policy with AllowBasicAuthPowershell and AllowBasicAuthWebService enabled for the Veeam service account.
To create a new authentication policy named "Allow Basic Auth":
New-AuthenticationPolicy -Name "Allow Basic Auth"Set-AuthenticationPolicy -Identity "Allow Basic Auth" -AllowBasicAuthPowershell
Set-AuthenticationPolicy -Identity "Allow Basic Auth" -AllowBasicAuthWebServicesWhere <UserIdentity> is the Veeam service account.
Set-User -Identity <UserIdentity> -AuthenticationPolicy "Allow Basic Auth"1.b. Sharepoint Permissions
Configuring Permissions for SharePoint Online.
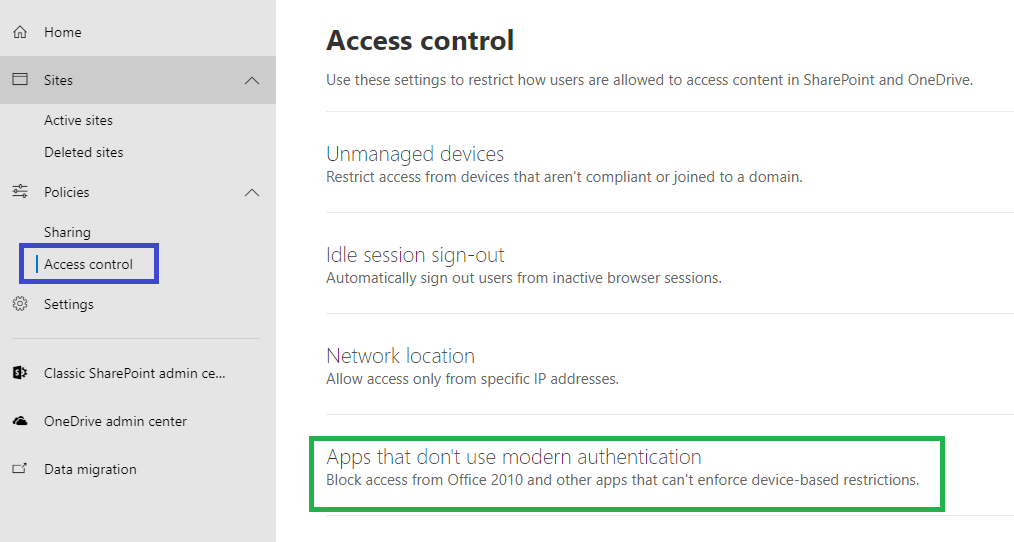
- Grant Veeam service account with the SharePoint Administrator Role in Azure Admin Center.
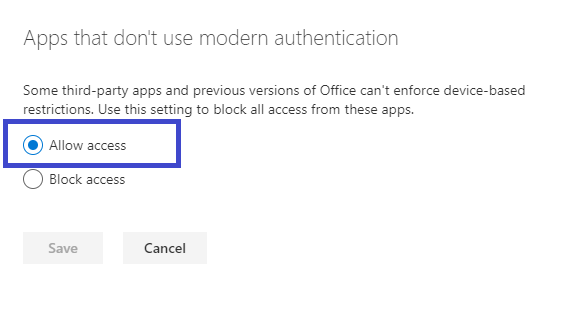
- In the SharePoint Admin Center open [Policies] > [Access control] and set "Apps that don't use modern authentication" to "Allow Access".
2. Configure the App password
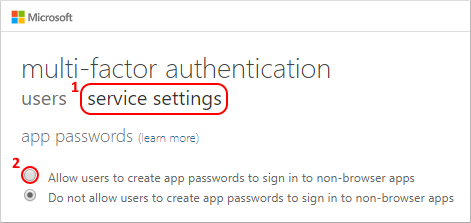
- Set up Veeam service account user to leverage Multi-Factor Authentication.
- Make sure users are allowed to create app passwords.
- Sign-in to https://portal.office.com using Veeam service account credentials and create app password.
3. Azure AD Application permissions
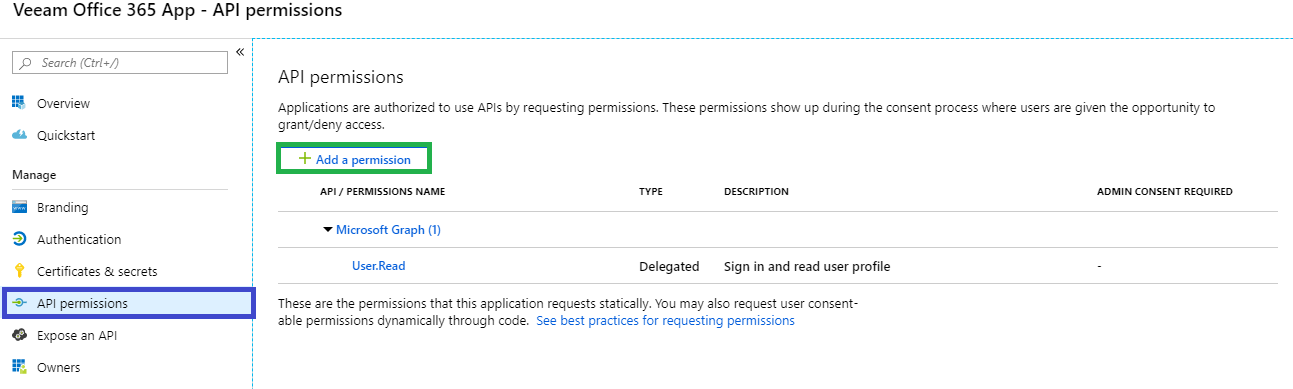
- Register a new application in Azure AD
- Go to API permissions and click [Add a permission].
- Configure the permissions per the "Requirements for Modern App-Only Authentication" section of this User Guide page.
All permissions must have Application type.
For more information about permission types please visit https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-permissions-and-consent
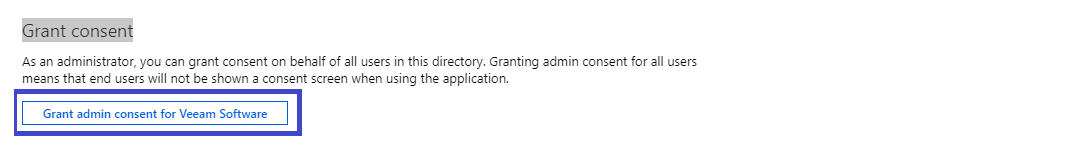
- After all API permissions have been added you will need to grant admin consent.
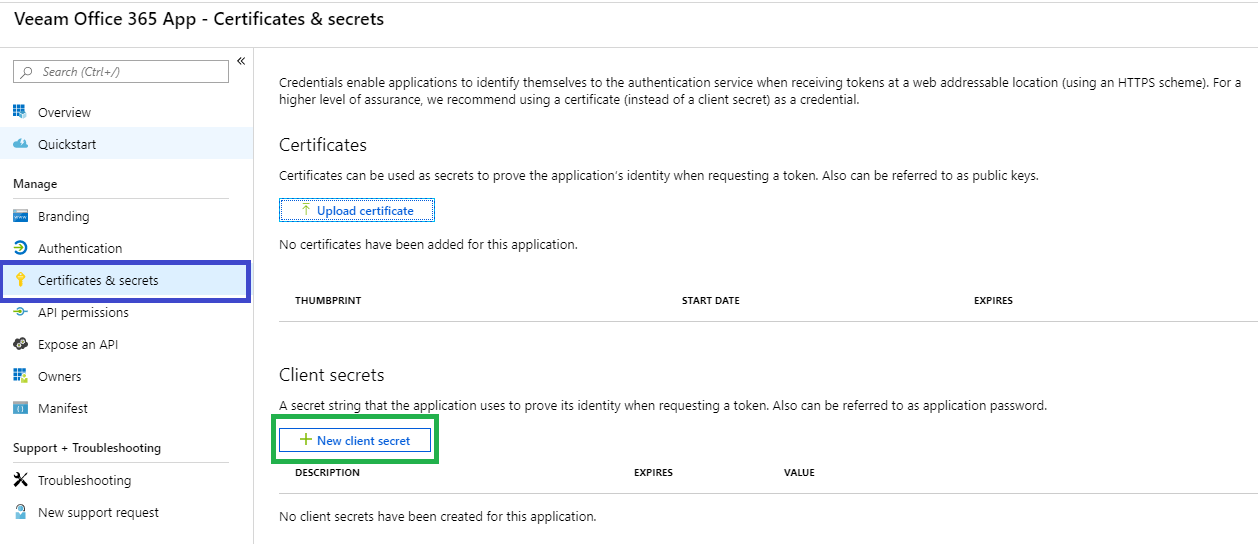
- Select [Certificates & secrets] and [+New client secret].
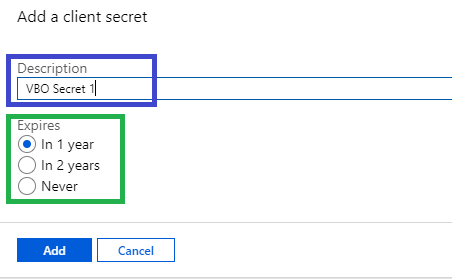
- Add a Description> Choose Expiration> Add.
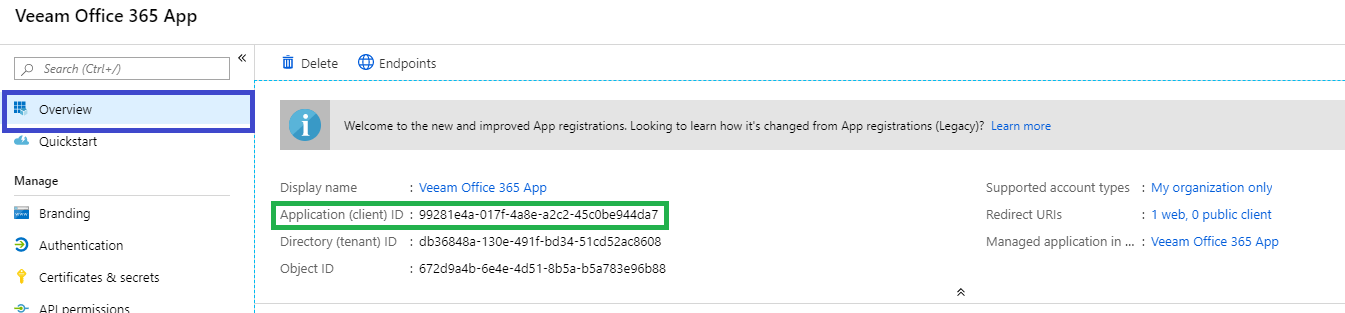
- Copy the Client's secret value.
- Go to Overview and copy the Application (client) ID.
Basic Authentication
When you add an organization using the basic authentication method, you are required to provide a user name and password to authenticate to your Microsoft 365 organization.
Exchange
Exchange permissions should be configured the same way as in the Exchange section of this article.
SharePoint
SharePoint permissions should be configured the same way as in SharePoint section of this article.
To report a typo on this page, highlight the typo with your mouse and press CTRL + Enter.
Spelling error in text
Thank you!
Your feedback has been received and will be reviewed.
Oops! Something went wrong.
Please, try again later.
You have selected too large block!
Please try select less.
KB Feedback/Suggestion
This form is only for KB Feedback/Suggestions, if you need help with the software open a support case
Thank you!
Your feedback has been received and will be reviewed.
Oops! Something went wrong.
Please, try again later.