Online Registration Launch
- Data Security
- Ransomware Backup
Radical Resilience Against Ransomware
- Relentless security
- Reduce your attack surface
- Recover from anywhere, to anywhere
- Access world-class incident response

- Ransomware Recovery
- Overview
- Veeam’s Approach to Ransomware
- Capabilities
- Solutions
- Latest Trends & Insights
Ransomware Confronted, Contained, Conquered
Relentless Security
Defend your data from an attack with secure backups and AI-powered malware protection.
Reduce Your Attack Surface
Keep malicious tampering at bay with end-to-end encryption and immutability.
Recover From Anywhere to Anywhere
Restore anywhere, from on-premises to the cloud or both, and get your business running 5x faster.
Backup is Easy, Recovery is Hard
weeks
Veeam’s Approach to Ransomware
Relentless Security
Early threat detection, SIEM integration, and proactive threat hunting, coupled with Veeam’s immutability, backup verification, secure access, incident response, and forensic triage, create a relentless security approach.
Reduce Your Attack Surface
Harden your infrastructure with Security & Compliance Analyzer and data best practices while monitoring for errors and anomalies. I/O Anomaly Visualizer ensures the lowest possible data loss, thanks to Veeam Continuous Data Protection.
Recover From Anywhere
to Anywhere
Meet your RTOs while ensuring you avoid reinfection with YARA content analysis. Let automation take the wheel for time-intensive tasks like documentation, testing, and verification so that you can restore your data from anywhere and back to production 5x faster.
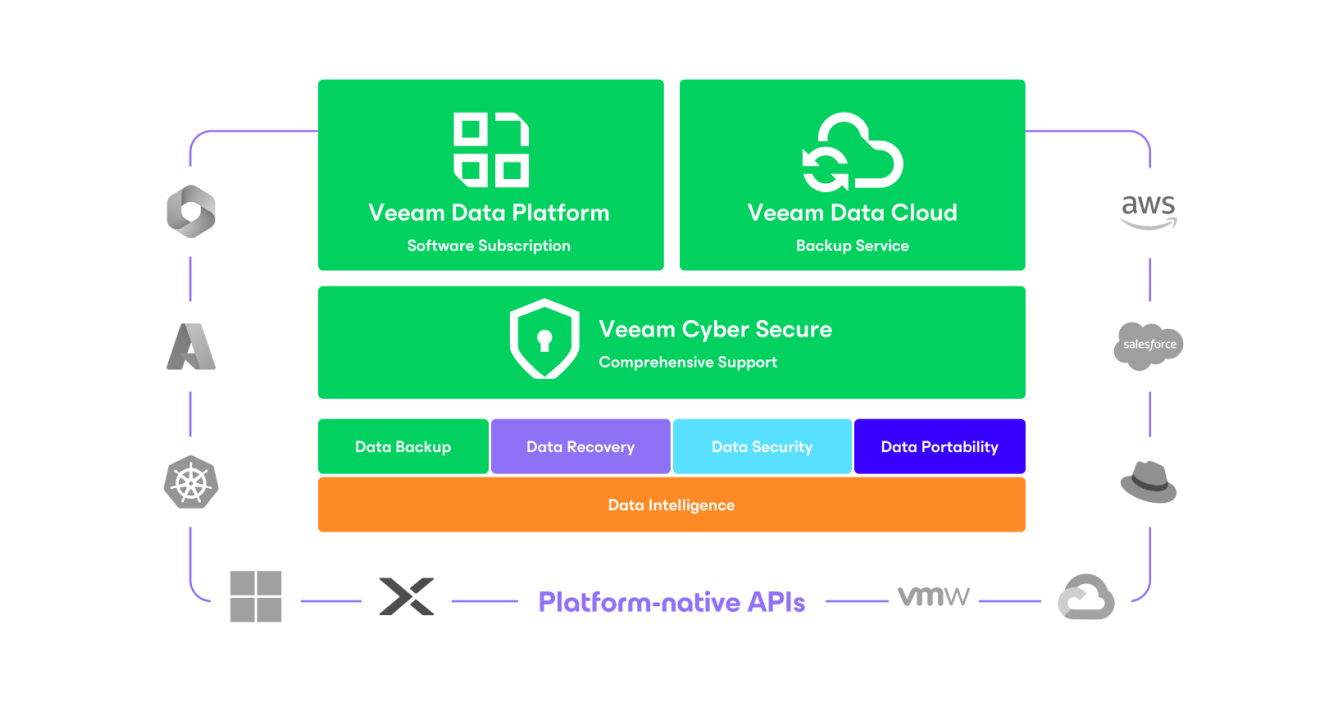
Secure Backup is Critical to Your Cyber Resiliency
Multi-layered protection, designed for your peace of mind

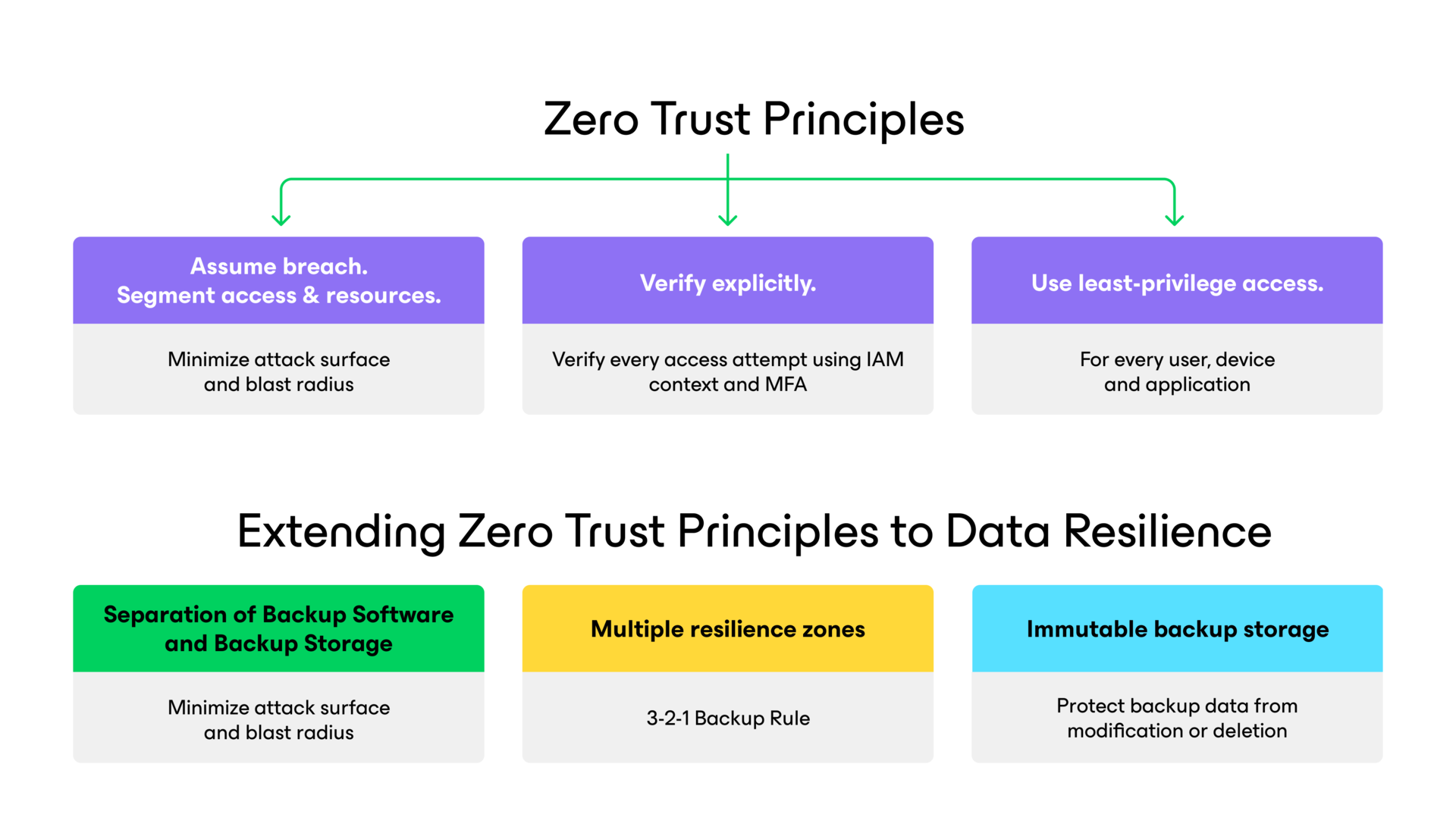
Extend Zero Trust to Data Backup and Recovery
Zero Trust is a highly effective strategy for better securing IT infrastructure against ransomware and cyber security threats. Data backup and recovery systems are critical and must be included in cyber resilience strategies, including Zero Trust initiatives.
- Assume breach & segment access
- Verify explicitly
- Least privilege access
Unify Your IT and Cybersecurity Teams for a Robust Ransomware Resiliency Approach
Early Threat Detection
Our AI-powered, built-in Malware Detection Engine performs low-impact inline entropy and file extensions scans during backup for immediate detection of suspicious activities and anomalies.
Proactive Threat Hunting
Quickly flag backup inconsistencies and report them into ServiceNow and your preferred SIEM tools so you can immediately act and reduce further risk to your data. Reduce response time with bi-directional ServiceNow incident lifecycle support, powered with 300+ unique alarms.
Get a Second Opinion
Allow your detection and response solution to report infections directly into the Veeam Incident API, marking existing restore points as infected or triggering a backup.
Put the Spotlight on Malware
Utilize the Veeam Threat Center, our one-stop, security-at-a-glance dashboard, that highlights threats, identifies risks, and measures the security score of your backup environment. Powered by VeeamONE.
World-Class Incident Response
Veeam Cyber Secure customers rely on the same incident response team that companies around the globe turn to when preparting for or under cyberattack. Get 24x7 response time and a 15-miunute SLA.
Avoid Reinfection
Identify ransomware strains and prevent the reintroduction of malware into your environment with YARA content analysis.
Zero Trust Data Resilience
Minimize the attack surface with the separation of backup software and storage and multiple resilience zones.
Instant Recovery, Anywhere You Need It
Access your data when you need to with dependable restores that work seamlessly across clouds and platforms so you can hit your SLAs.
Stay Secure with Veeam Cyber Secure including Coveware by Veeam Incident Response
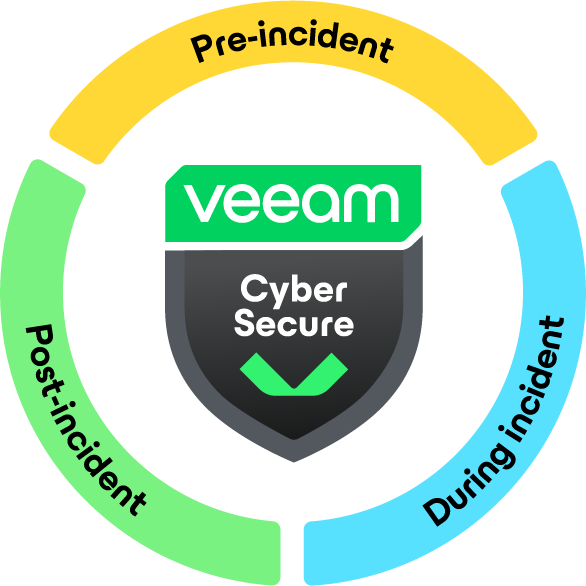
Pre-Incident
Proven security best practices and advanced onboarding support to ensure you have Veeam implemented to the highest security standards.
During Incident
As a premium Cyber Secure customer, your organization will become a retained client with Coveware by Veeam. You’ll have world-class experts on-call, helping you understand the best path forward. In the case of a cyber attack, Coveware retainer clients receive:
- A 27/7/365, 15-minute response SLA
- Coveware handles the incident from end to end – including triage with patent pending software, negotiations, settlement services (if needed), and assistance with recovery via decryptor software (included with the retainer).
- Retainer clients also receive unlimited learning and development for proactive training – suited for executive, board, and technical audiences.
Post-Incident
Know you’re covered with a Ransomware Recovery Warranty that covers up to $5 million USD in data recovery expense reimbursement.
Data Protection Starts With Trust
Data security is foundational to our approach.
We make sure everything you do with us is safe and secure so you can focus on what you do best – keeping your business running.
Know the Latest Ransomware Trends

2024 Ransomware Trends Report
Lessons learned from 1,200 victims and nearly 2,500 cyberattacks.
2024 Data Protection Trends
Our 5th annual report of data protection strategies of up to 13,300 organizations between 2020-2026.
Zero Trust Data Resilience Strategies
Begin building toward stronger enterprise data protection.
Ransomware Recovery Maturity Assessment
Find out how your ransomware recovery strategy compares to best practices.
Building a Cyber-Resilient Data Recovery Strategy
Build stronger cyber resilience through Veeam Data Platform and the NIST Cyber Security Framework 2.0.
FAQs
How does ransomware backup and recovery software work?
What are the best practices for ransomware backup?
Why choose Veeam for ransomware backup and recovery?
How often should I back up my data to protect against ransomware?
How do I protect myself against Ransomware using Ransomware Backup?
What are immutable backups?
How can I recover from Ransomware?
Radical Resilience is Our Difference
hybrid cloud and the confidence you need for long-term success.
Learn the Latest Trends in Data Protection
Our 5th annual report summarizing data protection strategies
Request Custom Demo
Oops! Something went wrong.
Please, try again later.
Contact us
Oops! Something went wrong.
Please, try again later.