Anyone with console access to a Linux machine can get root access on the machine by booting into “single user mode”. In this blog, I will show how to boot into single user mode and how to protect the bootloader against unauthenticated attempts to boot into single user mode.
Usually, single user mode is used when someone forgot the administrative credentials for a Linux system or troubleshooting. Another reason could be that someone locked down a Linux system in a way as described in the “Installing Ubuntu Linux for Veeam Hardened Repository”. In that case, there is intentionally no active root account configured and the only user on the system has no (or very limited) sudo permissions.
Booting Into Single User Mode
This example shows how to boot Ubuntu 20.04 into single user mode. It works the same on Ubuntu 22.04, but a bit differently on Red Hat (RHEL) derivates.
The first step is to select the boot option (“Ubuntu” in this case). Press “e” to edit the boot entry.
In the editor, search for the line that starts with “linux” and has parameters like root=/dev/disk-device (1). Change the “ro” to “rw” and add “init=/bin/bash” (3) at the end of the line. Changing the “ro” to “rw” mounts the file system automatically “read write”, which removes the requirement to remount the file system later manually to “read write”.
Then press CTRL+X or F10 to continue the boot process. Success: Now you have a root prompt without knowing the root password. Now you can add, for example, the Veeam Hardened Repository user to the “sudo” group to reconfigure things or do troubleshooting. Run the following command to do that (replace “veeamrepo” by the username you are using):
adduser veeamrepo sudo
Or you can set a new root password by using the “passwd” command and entering a new root password. Once you are done with your modifications, you can continue booting the system by typing:
exec /sbin/init
You can also reboot the system by using CTRL + ALT + DEL key combination.
Protecting Against Unauthenticated Users Booting Into Single User Mode
As shown above, by default, anyone with console access can get root / administrative permissions on a Linux system. Of course, one can protect against this. It is one of the requirements of DISA STIG hardening guidelines. In this example, I will show how to do this with Ubuntu 20.04. The description can be adopted by later Ubuntu versions as well. DISA STIG V-238204 requires:
“Ubuntu operating systems when booted must require authentication upon booting into single-user and maintenance modes.”
Achieving this requirement is a three-step process:
- Create a password with “grub-mkpasswd-pbkdf2”
- Add a username plus the password hash to /etc/grub.d/40_custom
- Update the grub (the bootloader) configuration
Creating the password hash is done by the grub-mkpasswd-pbkdf2 command. To keep it simple, I recommend doing this operation via SSH where you have the option to copy and paste with your mouse. The result looks like this:
veeamrepo@secureboot:~$ grub-mkpasswd-pbkdf2 Enter password: Reenter password: PBKDF2 hash of your password is grub.pbkdf2.sha512.10000.C0F70D240A8BC5C1BC4E1303EC4F040957C1AF1BB8E99EED573133D3A017BE9B2BB48E52577A141B3A6952527A9D1BEF13E2BB29978DA71F2D867EBB03545021.C4E81CAE7B464E78B15DF0A578B63BAB3A0CB180C311AFA5A85F6245800D11D40B37B817C3F30348EE603AF725B7E09B98A291114B0206D[…]
The hash (beginning with ”grub.pbkdf2.sha512”) is needed in the second step. Mark the hash with the mouse, which will copy it to the clipboard (you can check by pasting it into an editor of your choice).
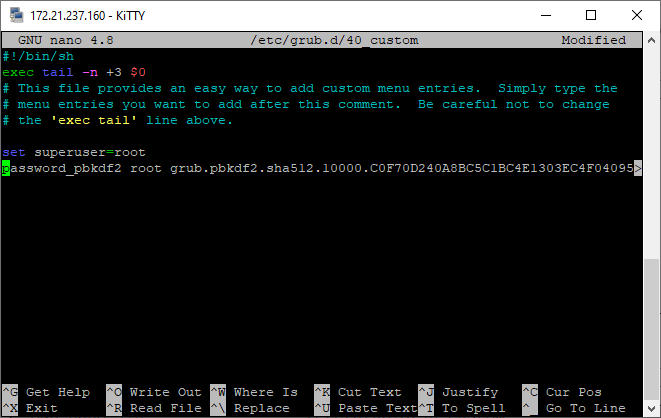
For the second step, open the /etc/grub.d/40_custom file with nano:
sudo nano /etc/grub.d/40_custom
At the end of the file, add two new lines (root can be replaced by any username you like):
set superusers=root password_pbkdf2 root grub.pbkdf2.sha512.10000.C0F70D240A8BC5F[…]
Paste the hash from above with “right click”. The result should look like the screenshot below. Save the file by pressing CTRL+X and confirm with Y.
Finally, update the grub bootloader configuration with:
sudo update-grub
After rebooting, the system will require you to enter the password. Without the password, the system will not boot. This behavior may or may not be desired, depending on your intent.
To require a password only when manipulating boot entries, one can edit the /etc/grub.d/10_linux file. Open it with nano “sudo nano /etc/grub.d/10_linux” and search for a line that starts with “CLASS=”. Add “- -unrestricted” inside the quotation marks at the end of the line. The result should look like this:
CLASS="--class gnu-linux --class gnu --class os --unrestricted"
Again, save the file by pressing CTRL+X and confirm with Y and update the grub bootloader with:
sudo update-grub
If you reboot now, the system will boot without asking for credentials. If you try to edit a boot menu entry to boot into single user mode, then it will ask for credentials.
Summary
If there is no password set for the grub bootloader, it’s easy to get administrative permissions on Linux. Setting a grub bootloader password is possible to prevent that. Just remember, setting a ah, bootloader password does not help against booting from another boot media to get around it or destroying all data by reconfiguring the RAID controller via out-of-band management.