Ransomware: every admins’ worst nightmare. And when one strikes, everyone starts blaming someone else. The security admin points the finger at the network admin for allowing the attack into the network. The network admin accuses the storage admin for not having more secure write access to the storage. In the end though, the business is going to want their data back regardless of who’s fault it is and guess who’s in charge of making sure that data was backed up? The backup admin. You may have several roles in your infrastructure but when ransomware hits, the backup admin is at the front of the line to get the data restored as quickly and with as little loss as possible. This series will give you some insight on existing and new features Veeam offers to turn this disaster event into you being the hero.
Protect your Veeam Backup & Replication console
Here is something you don’t always think about — protecting your Veeam Backup & Replication console. But even the server backing up your environment needs to be protected from attacks like ransomware and people with the best or malicious intent. Sure, you could consider encrypting your backups or taking your storage off the domain but not what could be compromised if you do not protect your Veeam server. This allows domain administrators access to the console without stopping to consider who is a domain administrator in your organization. Maybe consider that everyone who has access to the Veeam server does not need the ability to create/modify jobs or restore sensitive information. We would like to promote the concept of least privilege when it comes to Veeam and its components. This article will discuss some simple ways to lock down your Veeam server to help protect it from internal and external forces.
Separate user accounts and password policies
The user who opens the Veeam console does have to be a local administrator, but it does not have to be every local administrator. By default, Veeam is configured to allow anyone in the local administrators group full access to the Veeam console. By default, Windows machines added to the domain add domain administrators to the local administrator group. This is convenient when Veeam is first installed and you need to get the console set up. The next step should be to decide who should have access and why. Veeam has separate roles to assign to each user depending on what job they will be performing. It is also important to follow proper password change policies for accounts that have access to do operations in Veeam. This is especially the case if someone leaves the company, as it is time to change the password.
Assign correct Veeam roles to users
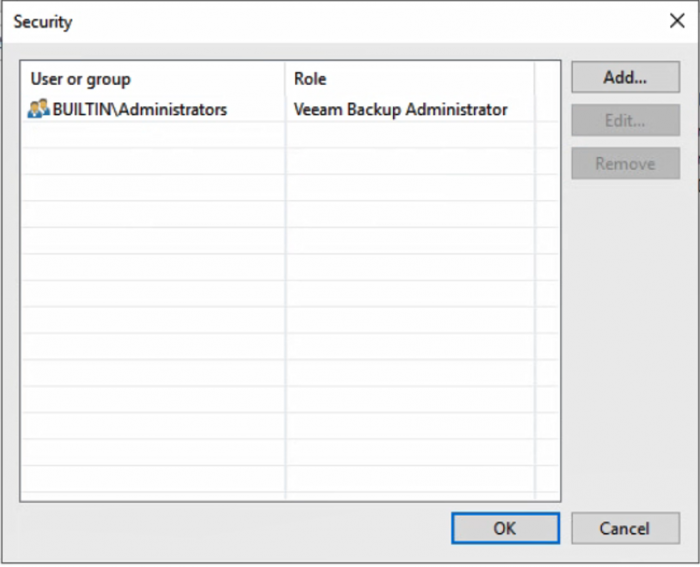
There are five roles that can be assigned to any user or group: restore operator, backup viewer, backup operator, tape operator and backup administrator. The restore operator role will allow a user to restore using existing backups or replicas. The backup viewer can only look at existing jobs and see session details but cannot restore. The backup operator can start and stop an existing job; they can also create VeeamZIP backups. The tape operator role allows the user to perform tape actions in the console: tape inventory, tape export, tape eject, tape catalog, inventory library, catalog library, rescan library, import tapes and eject tape from drive. The backup administrator role can perform every action in the console with no restrictions, which is why it is so important to limit the number of users who have this role.
These roles can help split up duties for users who do not need to have access to modify jobs. If you have an employee who needs to eject the tape for export off site on the weekends, that user also does not need the ability to restore sensitive company data. The backup viewer is a great role to give to an external auditor so that they cannot modify your jobs when checking if the console configuration meets regulatory requirements. Do not assign generic administrator accounts to any of the roles; if everyone is logging in as the same user then there is no way to retroactively tell who logged in and made changes to the console or performed an unauthorized restore.
To change the roles assigned to the users: click on the dropdown menu in the upper left-hand corner, select Users and Roles. Here, users can be added, edited and removed.
Benefit of local service accounts
The question on every IT administrators plate the last couple years is to put a machine on the domain or to not to put it on the domain. When it comes to Veeam Backup & Replication it does not greatly matter if it is or is not on the domain but there are extra configuration steps that need to be taken if it is added or removed after Veeam has been installed. Our configuration files for the software are set in the registry and when a machine is added or removed from the domain the machine name changes, meaning these registry keys need to be manually updated.
The pros for adding the Veeam Backup & Replication machine to the domain: centralized credential manager with Active Directory, easier to assign users to group roles, access to domain resources without extra steps and fast decommission of accounts for terminated employees. Adding the Veeam Backup & Replication server to the domain can make the administrators life easier and makes it easier to decommission accounts. The greatest downfall of a domain account is that the account is used to sign into more authentication forms, giving it a greater chance of being compromised and leaving an access point for ransomware to infect the environment. This can be mitigated with proper password resets, password strength and the concept of least privilege. Something to also keep in mind: if the Veeam Backup server is on the domain that does not mean the access to the repository has to be domain credentials. Keeping local service accounts as the only way to authenticate and store backups to a repository can also protect your backups: any Veeam backup chain can be imported into another console for restore.
Granularly assign responsibility
Veeam Backup Enterprise Manager is a web management console for your Veeam server. The enterprise manager has three roles that can be assigned to users: portal administrator, portal user and restore operator. The portal administrator has full access to all sections in the portal to the Veeam server. The portal user only has access to the machines within its scope to kick off backups and restores. The restore operator can only restore machines it has been given access to in the restore scope. The biggest advantage to assigning users roles from this portal is they do not have access to the full infrastructure, they can only manage or restore what they have been assigned. So, users can be delegated tasks without compromising other departments’ backup and restore scopes. This form of least privilege also protects the Veeam server from needing an additional login access point that could compromise the server.
Limiting the number of credentials that have access to the Veeam Server can help limit the number of potential access points that ransomware or any other malicious attack has to infect the Veeam server. Diversifying the types of credentials that have access to the Veeam server and its components can greatly reduce the spread of damage if there is a credential compromised. The next post in the series will cover what the 3-2-1 Rule is and why it is so very important.
Navigation:
- First step to protecting your backups from ransomware
- The 3-2-1 rule for ransomware protection
- 3 storage options against ransomware
- How VCSPs help against ransomware
- Are you prepared when ransomware does happen?
Helpful ransomware prevention resources:
- Identify and protect yourself against ransomware
- Try our Ransomware Prevention Kit
- Read Beat ransomware. 3 Ultimate strategies white paper
- Watch 3 Ultimate Strategies for Ransomware Prevention webinar
