Introduction
With the release of Veeam Backup for Microsoft 365 version 6, we have added a self-service restore portal. The restore portal offers authentication via OAuth2 at the organization’s Azure AD and therefore needs a secure connection between these two services.
This article is focused on environments where the backup administrator does not have global permissions in Azure AD to set up the necessary application registration for the restore portal of Veeam Backup for Microsoft 365 by using the built-in wizard. Azure AD administrators can use the described steps to manually prepare and create the application registration together with the backup administrator.
Please read all steps carefully before proceeding.
The recommended way to set up the application registration is to leverage the wizard built into Veeam Backup for Microsoft 365.
Prepare the Enterprise Application in Azure AD
This part must be done by the Azure AD administrator.
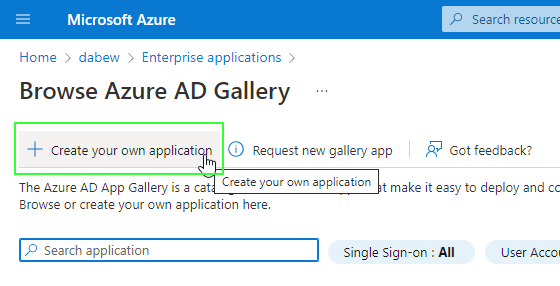
Give the new application a self-speaking name and select “Register an application to integrate with Azure AD (App you’re developing)”:
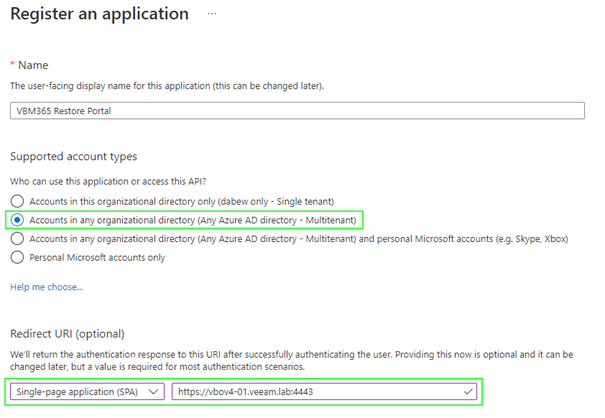
Select “Accounts in any organizational directory (Any Azure AD directory – Multitenant)” for the supported account types and add a single-page application (SPA) as redirection for your portal server. . Additional redirect URLs can be added later.
Switch over to the dependent App registration:
Note the Application ID since this will be needed later in Veeam Backup for Microsoft 365:
If additional redirect URLs are required, they can be added on the Authentication page:
In the Advanced settings on the “Authentication” page, you need to enable “Enable the following mobile and desktop flows:”
Select the “Certificates and secrets” page and upload a certificate (public key) you wish to use for this application. If you would like to use a self-signed certificate created by Veeam Backup for Microsoft 365, skip this step for now. A later section will discuss how to work with the self-signed certificate.
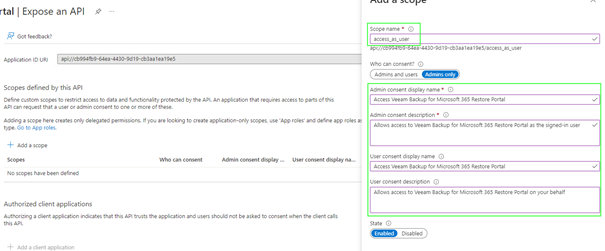
Select the “Expose an API” page to add a scope. The “Add a scope” wizard will provide an “Application ID URI,” and this needs to be accepted unchanged:
Set the scope name to “access_as_user” and provide display names and descriptions:
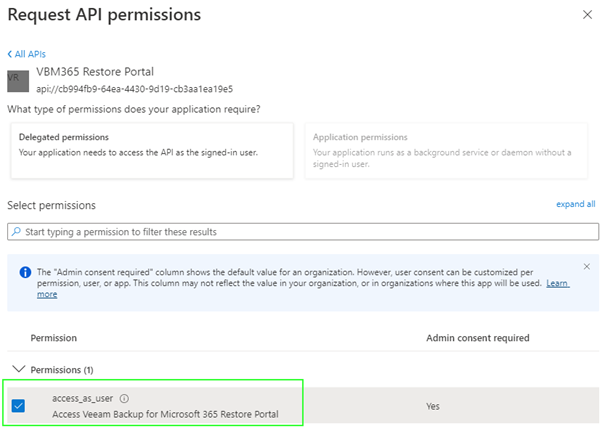
Go to the “API permissions” page and add a permission for the exposed API by selecting the API…
… and enabling the “access_as_user” permission:
Then select “Grant admin consent for …”:
Enabling the restore portal in Veeam Backup for Microsoft 365
This part must be done by the backup administrator.
Open the General Options in Veeam Backup for Microsoft 365:
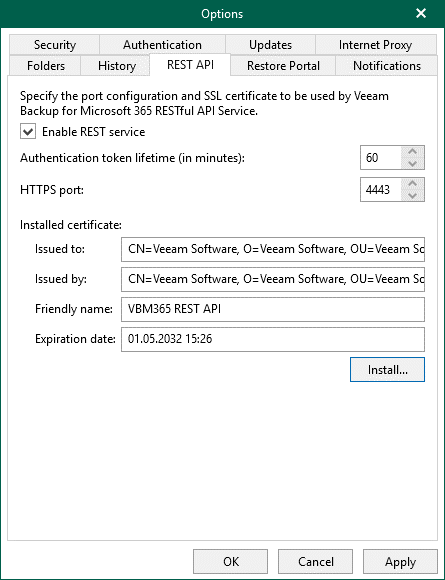
In the General Options, go to the REST API tab and enable the service, since this is the basic service for the Restore Portal to interact with the Veeam Backup for Microsoft 365 Server.
The REST service can also be installed on a separate host, which would be the recommended architecture for multitenant environments.
A self-signed certificate can be created or a prepared one selected through the “Install…” button:
Click on “Apply” and switch to the “Authentication” tab.
In the Authentication tab, enable the restore operator authentication:
As before, while enabling the REST service, reuse a certificate or create a new one. As a best practice, use a separate certificate for every use case.
Go to the Restore Portal tab, enable it and provide the Application ID noted in the steps above when preparing the Enterprise Application registration in Azure AD:
Ignore the “Create…” option to start a wizard, since this is about the manual way of setting up the Azure AD application. In general, we still recommend using the wizard if possible.
Create a self-signed certificate or select a prepared one with the “Install…” button.
If you have your own certificate prepared, this must be the certificate (private key) to the one that has been added to the Azure AD application registration in the preparation steps above.
If you used the self-signed option to create a new certificate, see the steps in the “Export and upload certificate” section below to add it to the Azure AD application.
After closing the General Options with “OK,” the Portal Service will be enabled and can be accessed through the URLs provided in the Azure AD applications redirection settings.
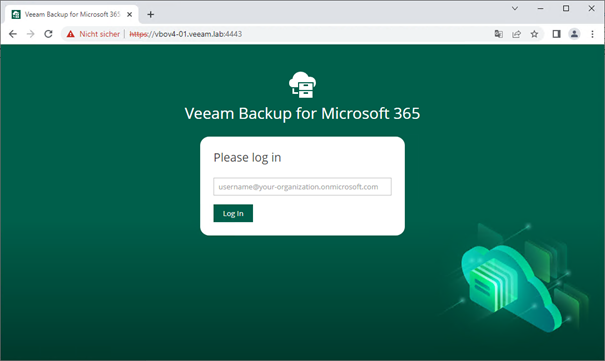
Open a web browser and use your URL to access the restore portal:
When logging in, you will be redirected to the OAuth authentication from Azure AD to authenticate:
If MFA is enabled for the user, this will be handled through Azure AD as well and is transparent for Veeam Backup for Microsoft 365:
After a successful authentication, the user will be redirected to the initially opened URL and the restore portal can be used:
Export and upload certificate
This part must be performed in cooperation by the backup administrator and Azure AD administrator.
If you used the option to create a self-signed certificate for the restore portal, you need to export the public key and upload this to the Azure AD application registration.
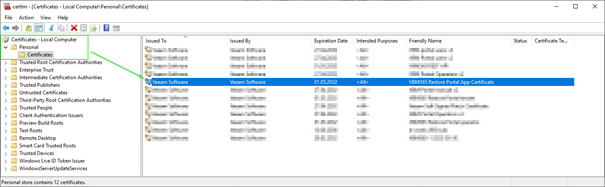
Open the certificate management on the Veeam Backup for Microsoft 365 server and find the desired certificate:
Right-click on the certificate and select “All Tasks” -> “Export…:
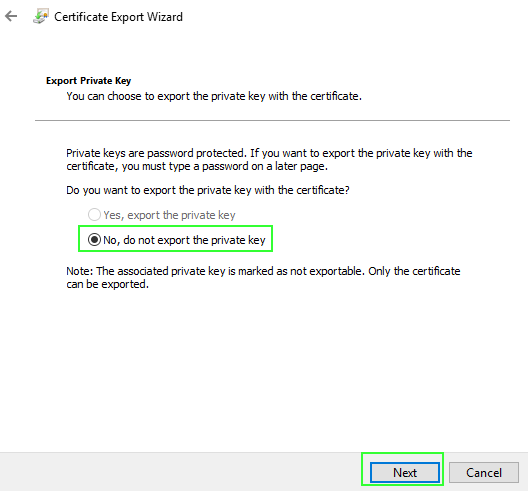
Click Next twice after reading the wizard instruction and the selection to not export the private key:
Select “DER encoded…” or “Base-64-encoded…” as the output format:
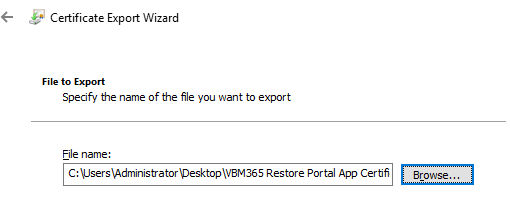
Provide a file name in which the public key should be exported and finish the export wizard:
In Azure AD, go to the “Certificates & secrets” page of the Application registration for the restore portal and upload the exported certificate file:
The certificate should now be seen in the list:
Conclusion
This detailed procedure has given the knowledge to set up the necessary application registration in Azure AD for the restore portal of Veeam Backup for Microsoft 365 without using the built-in wizard. For further information please see the Veeam Helpcenter pages or contact our support.
Appendix A – Azure AD App registration JSON Manifest
is the JSON Manifest for the created Azure AD Application registration. All Identifiers, Keys and IDs have been anonymized with “ANYTHING”. This JSON manifest could be used by Azure AD administrators to create the application registration after being modified to the individual needs and identifiers.
{
“id”: “ANYTHING”,
“acceptMappedClaims”: null,
“accessTokenAcceptedVersion”: null,
“addIns”: [],
“allowPublicClient”: true,
“appId”: “ANYTHING”,
“appRoles”: [],
“oauth2AllowUrlPathMatching”: false,
“createdDateTime”: “2022-05-02T12:45:45Z”,
“description”: null,
“certification”: null,
“disabledByMicrosoftStatus”: null,
“groupMembershipClaims”: null,
“identifierUris”: [
“api://ANYTHING”
],
“informationalUrls”: {
“termsOfService”: null,
“support”: null,
“privacy”: null,
“marketing”: null
},
“keyCredentials”: [
{
“customKeyIdentifier”: “ANYTHING”,
“endDate”: “2032-05-01T13:40:24Z”,
“keyId”: “ANYTHING”,
“startDate”: “2022-05-01T13:40:24Z”,
“type”: “AsymmetricX509Cert”,
“usage”: “Verify”,
“value”: “ANYTHING”,
“displayName”: “VB365 Restore Portal App Certificate”
}
],
“knownClientApplications”: [],
“logoUrl”: null,
“logoutUrl”: null,
“name”: “VB365 Restore Portal”,
“notes”: null,
“oauth2AllowIdTokenImplicitFlow”: false,
“oauth2AllowImplicitFlow”: false,
“oauth2Permissions”: [
{
“adminConsentDescription”: “Allows access to Veeam Backup for Microsoft 365 Restore Portal as the signed-in user”,
“adminConsentDisplayName”: “Access Veeam Backup for Microsoft 365 Restore Portal”,
“id”: “ANYTHING”,
“isEnabled”: true,
“lang”: null,
“origin”: “Application”,
“type”: “Admin”,
“userConsentDescription”: “Allows access to Veeam Backup for Microsoft 365 Restore Portal on your behalf”,
“userConsentDisplayName”: “Access Veeam Backup for Microsoft 365 Restore Portal”,
“value”: “access_as_user”
}
],
“oauth2RequirePostResponse”: false,
“optionalClaims”: null,
“orgRestrictions”: [],
“parentalControlSettings”: {
“countriesBlockedForMinors”: [],
“legalAgeGroupRule”: “Allow”
},
“passwordCredentials”: [],
“preAuthorizedApplications”: [],
“publisherDomain”: “ANYTHING.onmicrosoft.com”,
“replyUrlsWithType”: [
{
“url”: “https://anything.cloud.veryimportant:4443”,
“type”: “Spa”
},
{
“url”: “https://restore.internal.veeam.lab:4443”,
“type”: “Spa”
},
{
“url”: “https://ANYTHING.veeam.lab:4443”,
“type”: “Spa”
}
],
“requiredResourceAccess”: [
{
“resourceAppId”: “ANYTHING”,
“resourceAccess”: [
{
“id”: “ANYTHING”,
“type”: “Scope”
}
]
},
{
“resourceAppId”: “00000003-0000-0000-c000-000000000000”,
“resourceAccess”: [
{
“id”: “ANYTHING”,
“type”: “Scope”
}
]
}
],
“samlMetadataUrl”: null,
“signInUrl”: null,
“signInAudience”: “AzureADMultipleOrgs”,
“tags”: [],
“tokenEncryptionKeyId”: NULL
}