Read the full series:
|
Ch.1 — Backing up Domain Controller |
This is the 3rd article from my Active Directory protection series. In the previous one, I covered the domain controller recovery process. However, I believe that is a less common operation when compared to other Active Directory requests system administrators constantly receive. Among those requests, I believe the most frequent is Active Directory objects change.
That’s why today, I’d like to talk about Active Directory objects recovery and Active Directory tombstone objects reanimation when using old systems with the forest functional level of Windows Server 2008 and older. Fortunately, it’s a rare case now, but I wouldn’t be surprised to find examples of these systems still being around. Newer systems and features like Active Directory recycle bin are going to be covered in the next article in the series.
Active Directory objects life cycle
Ok, so why is it important to remember old cases? Because modern logic and features don’t work there. Prior to Windows Server 2008 R2, an Active Directory object lifecycle looked like this:
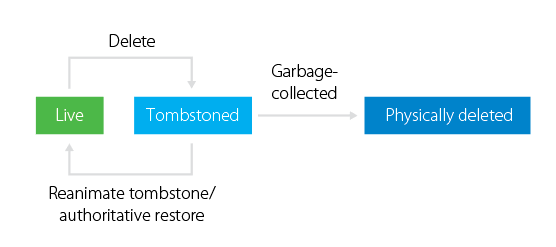
Once the Active Directory object is deleted, it is not hard deleted from a system. As you may know, Active Directory makes the object hidden by changing its attribute isDeleted to TRUE value. Then, it drops most of the objects’ attributes, renames the object, and moves it to a special container (CN=Deleted Objects). From now on, the object has a tombstone status, and standard Active Directory utilities don’t see its presence. Then, the object is conserved within this special state for a lifetime period (60 days for Windows Server 2000/2003 and 180 days for Windows 2003 SP1/2008). This is to ensure that the information about removal was successfully replicated across the system. Once the tombstone lifetime period is over, a special process called garbage collector physically removes the object from the database.
Here comes the question. If the tombstone object was not physically deleted within a certain amount of time, would it be possible to recover (reanimate) it? The short answer is yes. Even though the tombstone mechanism was never intended to be a temporary recycle bin, and objects weren’t ever supposed to be reanimated, the possibility exists and I’m going to show how you can do that.
Reanimating AD objects with LDP utility
LDP (LDP.exe) is an old and robust program that works with Active Directory, designed by Active Directory developers. It might look a bit ordinary, but it is very powerful and can give you full control under Active Directory objects. As a downside, you should invest quite some time into learning the program functionality, and it’s not quite obvious and modern.
To recover a deleted (tombstone) object using LDP, you should:
- Run this program (Start – Run – ldp)
- Connect it to a domain controller (Connection – Connect..)
- Use the appropriate (domain or enterprise administrator) credentials to authenticate. (Connection – Bind..)
- Search for a sought-for object (Browse – Search) within the Deleted Objects container. You will have to apply searching options and filters the smart way (check the figure 2 below). When navigating via Controls dialog, make sure you select the “return deleted objects” option, then press check in to add the object identifier for this option to the Active Control list. Then, save your settings and run the query to find tombstone
- Reanimate the tombstone object by using (Browse – Modify) a wizard to find the object via its distinguishedName (DN) parameter and remove its isDeleted value with object renaming, so the object is recovered back and you can see it from Active Directory Users and Computers snap-in.
The picture below shows a typical search I performed to find tombstone objects in my test domain:
As this article isn’t intended to be an ultimate guide for LDP utility, here’s an LDP guide, which will help you master your skills.
In addition to above, keep in mind that even when you reanimate tombstone objects this way, some object attributes (group membership for example) are dropped within an initial deletion, so they aren’t going to be recovered with reanimation and it might bring you a headache.
Using Veeam Explorer for Microsoft Active Directory
As an alternative to the approach above, it’s possible to utilize Veeam solutions and Veeam Explorer for Microsoft Active Directory in particular. This utility allows you to perform reanimation much faster and easier – and addresses many downsides of tombstone reanimation, with which you lose account password and many important object attributes (for example, user’s last and first name attributes are not saved in tombstone objects).
Yes, in order to use Veeam Explorer for Microsoft Active Directory you should have a backup copy of your DC where deletion happened. Yes, your domain controller should be virtualized, thus eligible to be backed up by Veeam Backup & Replication in the first place. That’s why it wouldn’t suit every scenario, since some preliminary steps are required. However, if you’re a lucky administrator of a virtual domain controller with a forest functional level of Windows Server 2003 or Windows Server 2008, read carefully. The information below will be helpful for you.
- Make sure you have a backup of your Domain Controller, processed with the application-aware processing option enabled (I explained the importance of it in the first article)
Figure 3. Veeam Backup & Replication, editing Backup Job - When the deletion happened and you would like to reanimate the object, navigate to the DC backup and select “Microsoft Active Directory objects…” to start the actual recovery and launch Veeam Explorer for Microsoft Active Directory.
Figure 4. Launching Veeam Explorer for Microsoft Active Directory - Browse to the required container and enable “compare all objects” and “show changed objects only” to make a pre-selection and force Veeam Explorer to compare the backup data with the real DC condition and display only changed items. See object status and don’t miss the “tombstone” one.
Figure 5. Veeam Explorer for Microsoft Active Directory, comparing objects - Restore the required object(s) back to the production or export them as an .lde file.
Figure 6. Veeam Explorer for Microsoft Active Directory, granular restore options - Note: you will be prompted to specify password restore options if recovering a user account. This way you can: restore an account with an old password, set new password manually or not restoring password at all. Restoring an old password might be helpful for reducing the administrator’s load and keeping the deletion incident in secret. Imagine dropping an entire organizational unit (OU) with hundreds of users during the night and then having to restore it. In the morning, all personnel will be prompted to change their passwords upon login, and they will also start asking questions. Clearly, it’s a good idea to avoid such a situation if possible.
Figure 7. Veeam Explorer for Microsoft Active Directory, specifying password restore options
Considering the steps above, you can see that Veeam Explorer for Microsoft Active Directory provides a relatively simple method of recovering tombstone Active Directory objects. If you by any chance run such an environment, don’t miss this product.
In addition to that, don’t forget that Veeam Explorer for Microsoft Active Directory is a very tiny part of overall Veeam Backup & Replication functionality. When selecting this product, you gain much more than Active Directory object recovery.
In the next article, I’ll compare Active Directory recycle bin with other methods of restoring AD objects.