Did you know that more than 90% of all successful hacks and data breaches start with a phishing scam? Do you even know what phishing is and how to protect your company from being victimized?
Phishing scams are attempts by cybercriminals to trick users into performing an action like clicking a malicious link, entering credentials, opening an attachment or even making changes to a company’s process. These scams are most commonly delivered as malicious emails, but they can also take other forms that usually drive a sense of urgency to get the user to click without thinking. They can result in ransomware, which includes the installation of malicious software (e.g.: viruses, Trojans, worms), stolen credentials, theft of money, data loss or even identity theft. A phishing campaign will exploit common human traits, like trusting people you know, in order to trick you into doing something that targeted users normally wouldn’t.
Prevent phishing attacks
If a phish is intended to trick you, then how can you protect your workforce from it? This seems like a moving target — and it is. Because phishers today are changing their tactics to trick people, it’s even more important than ever for you to prepare so you can always remain one step ahead.
You can prepare by enhancing your technical defenses and viewing your workforce as an extension of your security team. Having proper spam filters, a secure email gateway and using standard email authentication protocols (like DMARC, DKIM or SPF) and other technologies are all key to stopping phishing emails from making it into inboxes. That said, it’s still inevitable that your people will come face-to-face with phishing and it only takes one click from one person to potentially create havoc that requires your security teams to work overtime.
Wouldn’t you rather have your employees prepared to recognize and report a phishing email instead of clicking on it? I know I would. This is why I prioritize ongoing security awareness training. Train your employees on what phishing scams are and how to identify them. If possible, test their ability to identify suspicious messages and reward them when they spot them. Encourage your people to report suspicious emails to your security team, and this is even better if you have an easy way for them to do so. Don’t let phishing or security become a once-a-year topic; keep the conversation going.
Anatomy of a phishing attack
Once you commit yourself to preparing your workforce, you need to understand who you are up against. How does phishing work and what are the attackers going after?
The concept behind phishing is simple and not new. Remember getting a phone call telling you that you won some contest you didn’t remember entering? You may get so excited and tell the caller whatever was needed to get your prize. That same concept applies today with phishing; it’s just through email or another digital communication channel.
Phishers, who are really just scam artists that use digital communications, exploit common human traits, like trusting people they know, to trick them into doing something that they normally wouldn’t.
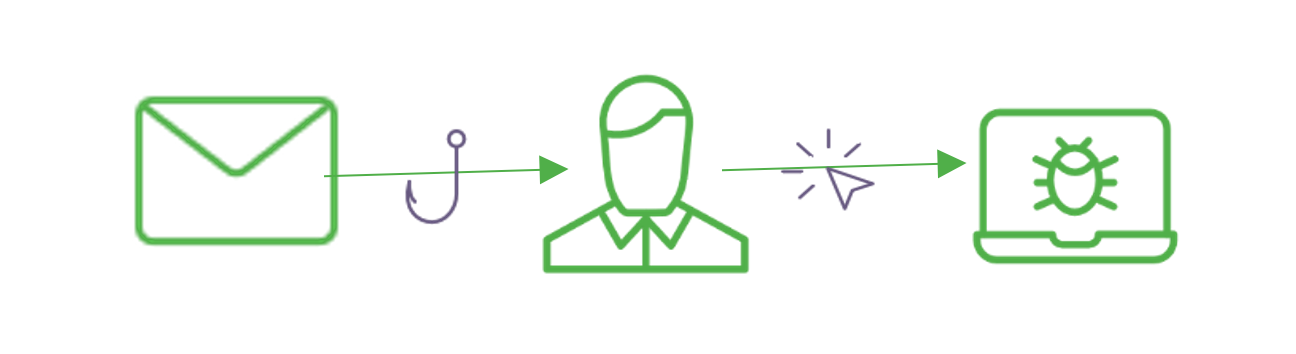
Email sent > Recipient falls for the lures > Recipient does intended action > Sensitive data is stolen, or computer is infected
For example, a successful phishing attack starts with an email to a recipient. Within this email are lures to try to convince the recipient to take whatever action is being requested. The emails usually contain hyperlinks or attachments, but not always. Hyperlinks typically point to malicious websites that ask for some type of personal details; some may even impersonate legitimate companies. Attachments usually contain some type of malicious code to infect the recipient’s computer or network. Emails that don’t contain either usually ask the recipient to either respond back to the email or call a number to share some information that the sender needs.
If the recipient falls for the scam, they often don’t realize it. They believe it was legitimate and something positive may even happen. However, the phisher has either stolen their information or money or perhaps infected their computer.
Different types of phishing attacks
All cyber criminals are not created equal. There are different types of phishes that you need to prepare everyone in your organization to look for. Here are a few common types:
Spear phishing
Spear phishing attacks are a targeted scam intended for a specific audience. You don’t receive the email by accident. The phisher has conducted specific research to find you and send you a message that would make sense to you. It could be because you are part of your company’s HR department, or maybe you have recently posted online that you were promoted.
Whaling
Whaling is a type of spear phishing that is targeted directly to the executives of a company, i.e., the “big fish.” A company’s executive team is usually public information and easily found on the company’s website. This makes them easy targets. Executive staff also tend to have access to sensitive information and make financial decisions, which makes them a lucrative target for phishers.
BEC and CEO fraud
Business Email Compromise (BEC) and CEO fraud is another form of spear phishing that seeks to impersonate your company or your company’s CEO. Knowing that people are quick to trust those in positions of authority, phishers will impersonate people who are likely to illicit compliance with a request. Company email domains are easy to spoof and official logos can be found online. The names of people who work at your company are also easily accessible through many social media sites. This makes it easy for phishers to focus on BEC.
Vishing
Vishing is phishing over the phone (it stands for “voice phishing”). This is essentially the scam phone calls that you receive today and have likely received even before you had a computer in your home. These traditional scams are successful because hearing a person’s voice helps you build a relationship with the caller. This makes it more difficult for you to not comply with the caller’s request.
Smishing / SMShing
Smishing, also known as SMShing, is a malicious text message (it stands for “SMS phishing,” where SMS refers to text messages). These are shorter versions of the more traditional phishing scams and usually contain a shortened hyperlink to fake websites with a short, to-the-point message urging action.
Phishing awareness: How do you catch a phish?
One of the most common first questions you may have is: how do I know if something is a phish? While we could get into all the technical ways of evaluating email headers, for general end users, employee awareness training provides awareness of some key warning signs. Even more important than the warning signs, you need to remind end users that if they have any doubts, they should do their homework and report suspicious messages to your security team for further investigation if they suspect a phish. Remember, a healthy dose of skepticism should be encouraged.
Phishing warning signs
What are the warning signs of phishing attempts? There are many, and they can change as phishers change their tactics. Generally, if your workforce notices a combination of any of these warning signs, they should proceed with extreme caution:
- Generic greetings or signatures
- Lacking sender or company information
- Pixelated or blurry images
- Phishing website links that don’t make sense
- Poor spelling or grammar
- Threats or urgent requests
- Email claims with offers that are too good to be true
- Requests for personal information like bank accounts or wire funds, to move money or change direct deposit information
- Unexpected email or attachments
- Mismatching subject and message
- No supporting communication
Help your users detect phishing by following these steps:
- Do your homework. Search online for information about the supposed sender. You can even search for the exact email you received and see if others have already tagged it as a scam.
- Confirm requests using a second method of verification. Never email the sender back by replying to suspicious emails. Use a separate method of communication, such as a phone number or email address from a recent bill, to contact the sender and confirm the request.
- Hover over links in the email and see if the hyperlink’s web address matches the company’s legitimate website domain. Type the web addresses into the browser if you think it’s a fake website but don’t click on the link itself.
- Look at the file name of attachments. Consider if you were expecting the attachment or need it. Never open an attachment that you are not expecting or one that ends with an extension you may not recognize (i.e., filename.exe when it says it is a Word document).
- Use your own judgement. Employee awareness training starts with using common sense to help identify if an email is legitimate or if it may be phishy.
Is the site legitimate or is it a phishing attack? Follow these tips:
- Check the web address. Is the company name in the URL spelled correctly? Does the address start with https instead of http? Just because it starts with https doesn’t mean it’s legitimate, it just means that it is a secure connection. But if it doesn’t start with https, that should at least be a red flag that the web pages should not be trusted with any sensitive information. Likewise, seeing a locked padlock or key in the address bar doesn’t always mean the site is legitimate. But if you don’t see one, don’t input any information.
- Look for pop-ups. If you go to a site and are met with an onslaught of pop-up ads, be cautious.
- Pay attention to the branding. Does the branding — i.e., the look and feel — of the site match what you would expect for the supposed company you are trying to visit?
What should you do if your organization falls for a phishing attack?
Remember, phishing scams are designed to trick you. You may have implemented the best anti-phishing countermeasures and phishing awareness programs, yet still have a user fall for a phishing scam. It happens. What’s most important is that you are prepared to respond.
Consider these recovery steps and work with your cybersecurity teams to build an appropriate response and recovery plan for your organization:
Contain potential exposure
If a user interacts with a malicious phishing email, try and isolate the machine and ensure that your cyber team gains access to investigate.
Change passwords
Force the user to change his password. If multiple passwords are used, it’s advised to change all of them as you may not know the extent of what may have been compromised.
Follow your incident response process
A phishing attack is a type of cybersecurity incident. Follow your incident response processes, which should include steps to identify the phishing email, locate it within other users’ inboxes, remove it from those inboxes, investigate the impact and triage it accordingly.
Look for malware
Use your monitoring tools to scan the user’s computer and your network for malware (e.g., malicious software such as viruses, Trojans or worms), suspicious activity or anomalies.
Personal protection
Depending on the nature of the phishing attack, if the user divulged any personal information, the user may want to set up fraud alerts with appropriate credit-monitoring bureaus. If the phishing attack spoofed or impersonated a real company, share that information with the other company so they can alert other users as well.
Take time to learn
As with any cyberattack, the lesson learned from an attack is often more valuable than the data the cybercriminal has stolen. Keep a list of lessons learned and evaluate your existing processes and controls to determine if you could do anything differently. Also, ramp up your phishing awareness even more for your users.
Summary
Phishing scams are the top cybersecurity attack vector by cybercriminals that rely on human psychology to convince a recipient to take some type of action. Get ahead of this attempt by setting up your defenses and preparing your employees to help spot a phish.
Additional resources:
