In today’s data-driven world, where information is your most valuable asset, protecting sensitive data has become essential for organizational security. The National Institute of Standards and Technology (NIST) provides a comprehensive cybersecurity framework (CSF) that assists businesses in safeguarding their data. By understanding and implementing this framework, organizations can enhance their cybersecurity posture and mitigate potential risks.
Overview and Benefit of the Nist Cybersecurity Framework
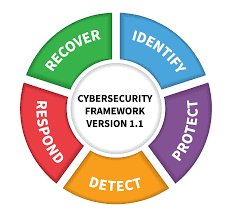
The NIST Framework for Data Protection provides guidelines, standards and best practices for securing data. It was developed by the National Institute of Standards and Technology, to help organizations establish robust cybersecurity programs and is based on five core functions: Identify, Protect, Detect, Respond and Recover.
Identify: this function focuses on understanding and managing data-related risks. It involves asset management, risk assessment and the development of a comprehensive understanding of the organization’s data landscape.
The framework enables organizations to take a systematic approach to identify and manage data-related risks. By implementing the Identify function, businesses gain a holistic understanding of their data assets and associated risks, allowing them to make informed decisions and allocate resources effectively.
Protect: this function aims to implement safeguards to ensure data confidentiality, integrity and availability. It covers activities such as access control, data encryption and security awareness training for employees.
Detect: the detect function involves continuous monitoring and proactive threat detection. It includes activities like security event logging, intrusion detection systems and anomaly detection.
The Protect and Detect functions of the framework help organizations establish proactive security measures. By implementing access controls, encryption and continuous monitoring, organizations can prevent data breaches or detect them at an early stage, minimizing the potential impact.
Respond: this function outlines the steps organizations should take in the event of a cybersecurity incident. It includes incident response planning, communication protocols and coordination with external stakeholders.
The Respond function equips organizations with the necessary tools and procedures to respond effectively to cybersecurity incidents. By developing an incident response plan, organizations can minimize the damage caused by an incident, ensure timely communication and restore operations efficiently.
Recover: the recover function focuses on restoring services and operations after a security breach. It involves backup and recovery strategies, conducting post-incident reviews and improving resilience for future incidents.
The Recover function focuses on ensuring business continuity after a security incident. By implementing backup and recovery strategies, organizations can swiftly recover data and systems, reducing downtime and maintaining operations.
How Veeam Can Help Implement the NIST Framework
Implementing the Cybersecurity Framework requires a structured approach. Veeam can assist companies in applying the NIST Cybersecurity Framework by offering several key features and functionalities. Let’s explore how Veeam can help organizations align their data protection practices:
Data backup and recovery: Veeam provides robust backup and recovery solutions that align with the NIST Framework‘s “Protect” and “Recover” functions. By implementing the Veeam Data Platform, organizations can create regular backups of their critical data, ensuring its availability and integrity. In the event of a cybersecurity incident, Veeam enables organizations to quickly recover data and restore normal operations, minimizing downtime and disruption.
Data encryption: encryption is a crucial aspect of data protection, and Veeam offers strong encryption capabilities to safeguard sensitive information. By encrypting data at rest and in transit, organizations can meet the requirement for protecting data confidentiality.
Access control and authentication: Veeam helps companies implement access control measures, another key aspect of the “Protect” function. With Veeam, organizations can enforce granular access controls, ensuring that only authorized personnel can access and modify data. Additionally, Veeam supports various authentication mechanisms, including multi-factor authentication, enhancing the security of data access.
Continuous data monitoring: the NIST Framework emphasizes the importance of continuous monitoring for early detection of potential threats. Veeam offers monitoring and reporting capabilities that enable organizations to monitor their data protection environment effectively. Organizations can proactively identify suspicious activities or anomalies that may indicate a security breach like a ransomware attack, allowing them to respond promptly.
Incident response and reporting: Veeam facilitates incident response planning and execution, aligning with the “Respond” function. Veeam’s solutions enable organizations to create comprehensive incident response plans, establish communication protocols and coordinate actions during security incidents. Veeam also provides reporting capabilities, allowing organizations to document and report cybersecurity incidents.
Integration with security tools: Veeam integrates with various security tools and technologies, enhancing an organization’s overall cybersecurity posture. By integrating Veeam with security information and event management (SIEM) systems, organizations can gain a holistic view of their data protection and security landscape. This integration enables better threat detection, response coordination and compliance reporting, aligning with the NIST Framework’s objectives.
Where Do I Start?
The Cybersecurity Framework is important to security because it provides organizations with a comprehensive framework for managing cybersecurity risks, improving their security posture and aligning with industry best practices. The first step in improving your security posture is to understand the risks specific to your organization. Conducting an initial assessment of your organization’s current cybersecurity posture will let you identify strengths, weaknesses and gaps in data protection measures. Once you know your environment, you can prioritize the implementation of NIST functions based on the risk to your critical data assets and create an implementation plan, outlining the activities, resources and timelines.
Veeam plays a vital role in helping companies apply the Cybersecurity Framework by providing comprehensive data protection solutions. By leveraging Veeam’s capabilities, organizations can enhance their data protection practices, mitigate risks and complete their cybersecurity posture. Finally, implementing Veeam’s solutions in conjunction with the Cybersecurity Framework empowers organizations to effectively protect their data assets and respond to cybersecurity incidents, safeguarding their valuable information. In a world where data is your most valuable asset, would you want to do anything less?